Hi all,
My third time uninstalling and reinstalling both Wiregard and Pihole in an attempt to get it working.
Here’s what I have;
mydomain.com pointing to my static public IP 111.222.33.44
my Odroid with Pihole and Wireguard at 192.168.20.19 on my network
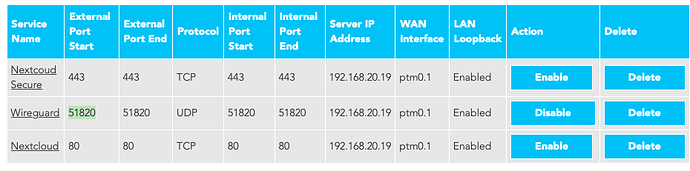
Nextcloud installed and available at mydomain.com/nextcloud when I have ports 80 & 443 open (I would prefer that Nextcloud was available at next cloud.mydomain.com but I’m so frustrated at the moment that I will aim for functionality first)
Port 51820 open on my router pointing at 192.168.20.19
Here’s what I want to achieve;
- Secure access to my Nextcloud instance from my laptop & phone from outside my network.
- Access to my Nextcloud instance from my desktop inside my network
- Ad-blocking from inside my network (and outside too if I can ever get it working)
- Ad-blocking on my phone (the cherry on top)
After the latest attempt to get it working I currently have;
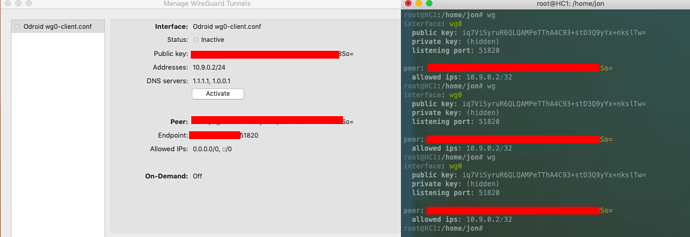
My wg0.conf
[Interface]
Address = 10.9.0.1/24
PrivateKey = **********************************************************
ListenPort = 51820
PreUp = /boot/dietpi/func/obtain_network_details
PostUp = sysctl net.ipv4.conf.%i.forwarding=1 net.ipv4.conf.$(mawk 'NR==3' /run/dietpi/.network).forwarding=1
PostUp = sysctl net.ipv6.conf.$(mawk 'NR==3' /run/dietpi/.network).accept_ra=2
PostUp = sysctl net.ipv6.conf.%i.forwarding=1 net.ipv6.conf.$(mawk 'NR==3' /run/dietpi/.network).forwarding=1
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o $(mawk 'NR==3' /run/dietpi/.network) -j MASQUERADE
PostUp = ip6tables -A FORWARD -i %i -j ACCEPT; ip6tables -t nat -A POSTROUTING -o $(mawk 'NR==3' /run/dietpi/.network) -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o $(mawk 'NR==3' /run/dietpi/.network) -j MASQUERADE
PostDown = ip6tables -D FORWARD -i %i -j ACCEPT; ip6tables -t nat -D POSTROUTING -o $(mawk 'NR==3' /run/dietpi/.network) -j MASQUERADE
# Client 1
[Peer]
PublicKey = *****************************************************f8So=
AllowedIPs = 10.9.0.2/32
# Client 2
#[Peer]
#PublicKey = XXXX
#AllowedIPs = 10.9.0.3/32
and my client.conf
[Interface]
PrivateKey = *******************************************************************
Address = 10.9.0.2/24
DNS = 10.9.0.1
[Peer]
PublicKey = ***********************************************************f8So=
AllowedIPs = 0.0.0.0/0, ::/0
Endpoint = 111.222.33.44:51820
If I connect the client to the VPN I do not get internet (stalls looking for DNS resolution)
Regardless of whether I am connected to the VPN I currently cannot find the Pihole web admin. I can’t find it at pi.hole/admin, 192.168.20.19/admin, 10.9.0.1/admin, or 111.222.33.44/admin
curl -I localhost returns;
HTTP/1.1 301 Moved Permanently
Location: https://localhost/
Date: Thu, 30 Jul 2020 11:30:39 GMT
Server: lighttpd/1.4.53
I would dearly like to get this sorted out within 1 week, before semester 2 starts - I’m going to be real busy and would love my notes and resources available in Nextcloud.
If this is not possible I will have to fall back on opening ports 80 and 443 on my router.
Hi,
Pls can you check using wg command if your client is connected. Did you set listen on all interfaces, permit all origin in Pihole?
Hi Joulinar
wg returns (when the client is connected)
interface: wg0
public key: xxx
private key: (hidden)
listening port: 51820
peer: xxx
allowed ips: 10.9.0.2/32
I also must add that I do not know what to do about the DNS settings in my macOS network preferences. I have my laptop set up currently with two ‘locations’ - pihole and no-pihole depending on whether I am on my home network or not.
I removed the keys from your post. Don’t post them on a public board.
I don’t think your client is not connected correctly. There is no message about last handshake. Which port did you forward on your router?
As well pls check log from the client if there are error messages.
Hi again,
Port 51820 is forwarded
Attached is the Wireguard log. I can’t see anything obvious for errors.
Regarding your earlier question about Pihole interfaces. Since reinstalling I have not changed anything because I can’t access Pihole admin
wireguard-log-2020-07-30T224513Z.txt (92.9 KB)
are you stopping your WireGuard VPN after a couple of minutes always? becasue I see this quite often happen.
2020-07-30 22:34:40.039526: [APP] Tunnel 'Odroid wg0-client.conf' connection status changed to 'connected'
2020-07-30 22:34:44.267478: [APP] Status update notification timeout for tunnel 'Odroid wg0-client.conf'. Tunnel status is now 'connected'.
2020-07-30 22:36:13.092335: [APP] startDeactivation: Tunnel: Odroid wg0-client.conf
2020-07-30 22:36:13.216242: [APP] Tunnel 'Odroid wg0-client.conf' connection status changed to 'disconnecting'
2020-07-30 22:36:13.489918: [NET] Network change detected with satisfied route and interface order [en0]
As well, are you located at home on same network? Or are you on a mobile network while testing?
Somehow I’m missing the handshake in your log. I don’t have on iOS device at hand to test, but in Win10 as well as Android I see this on my logs
Android
07-31 09:22:06.925 20810 21027 I WireGuard/GoBackend/WireGuard: Device started
07-31 09:22:06.963 20810 20837 D WireGuard/GoBackend/WireGuard: peer(BBBB…BBBB) - Sending handshake initiation
07-31 09:22:06.964 20810 20837 D WireGuard/GoBackend/WireGuard: peer(BBBB…BBBB) - Awaiting keypair
07-31 09:22:07.008 20810 20837 D WireGuard/GoBackend/WireGuard: peer(BBBB…BBBB) - Received handshake response
07-31 09:22:07.008 20810 20837 D WireGuard/GoBackend/WireGuard: peer(BBBB…BBBB) - Obtained awaited keypair
Win10
2020-07-31 11:21:35.753471: [TUN] [wg0-client3] Startup complete
2020-07-31 11:21:38.026162: [TUN] [wg0-client3] peer(BBBB…BBBB) - Sending handshake initiation
2020-07-31 11:21:38.043152: [TUN] [wg0-client3] peer(BBBB…BBBB) - Awaiting keypair
2020-07-31 11:21:38.208394: [TUN] [wg0-client3] peer(BBBB…BBBB) - Received handshake response
2020-07-31 11:21:38.210391: [TUN] [wg0-client3] peer(BBBB…BBBB) - Obtained awaited keypair
On your WireGuad server, you should see something like this if connection is working. There should be a handshake message as well.
root@DietPi4:~# wg
interface: wg0
public key: xxx
private key: (hidden)
listening port: 51820
peer: xxx
endpoint: x.x.x.x:49336
allowed ips: 10.9.0.6/32
latest handshake: 23 seconds ago
transfer: 1.53 GiB received, 1.50 GiB sent
- according to those timestamps yeah this is probably when I was trying different dns server settings in the client config file.
As well, are you located at home on same network? Or are you on a mobile network while testing?
Yes
I don’t have on iOS device at hand to test, but in Win10 as well as Android I see this on my logs
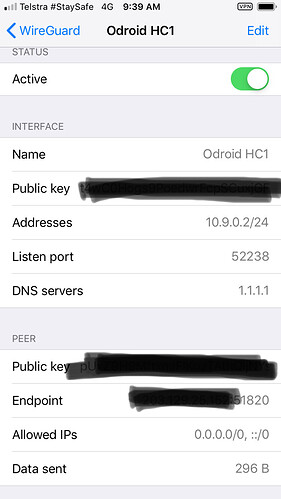
At this stage I am not setting up an iOS device (although I’d like to later). The client is my macOS laptop with the Wiregard client app.
There should be a handshake message as well.
root@HC1:/home/jon# wg
interface: wg0
public key: *********************************************************Tw=
private key: (hidden)
listening port: 51820
peer: ********************************************************8So=
allowed ips: 10.9.0.2/32
It seems important - first up - to figure out why I can’t find the Pihole admin anymore.
PiHole should not be your problem right now because you are missing the very first step, a valid VPN connection.
Still your wg output doesn’t show any handshake, means no VPN connection esteblished. Pls try to test with your macOS laptop from outside you local network (e.g. using a mobile phone as hotspot)
I get no internet access when connected to the client vpn and on my phone’s hotspot.
I tried both 192.168.20.19 and 1.1.1.1 in the client’s config file for DNS.
Can’t even ssh to the server
please put aside the DNS topic for the time being. First you would need to ensure that your WireGuard client is connecting correctly to you WireGuard server. And this, seems not the case at the moment. As long as wg is not showing any endpoint IP address, handshake and transfer data, your connection is not established.
root@DietPi4:~# wg
interface: wg0
public key: xxx
private key: (hidden)
listening port: 51820
peer: xxx
endpoint: x.x.x.x:49336
allowed ips: 10.9.0.6/32
latest handshake: 23 seconds ago
transfer: 1.53 GiB received, 1.50 GiB sent
Sure.
How?
Shall I uninstall both and start over?
If so in which order?
Do the clients not show any error message when (trying to) connect to the server?
The server can be reached otherwise, e.g. the webserver (Nextcloud) on port 80/443 via the same domain/hostname that you use in your VPN client configs right?
Then WireGuard must actually receive something, in case re-check WG logs. I mean initially it was working, the logs clearly show the connections, hence wg should show handshake/last connected entries as well for the clients you connected with.
There is no difference in the output of
sudo wg
when the client is either active or inactive
There are no error messages shown by the client.
The timestamps in the log are not correlating with the time on my laptop, so I’m not sure which time they are relating to?
Attached is the log from the short period when I connected the client to take those screenshots
Nextcloud is reachable at
mydomain.com when port 443 is opened on the router.
snippet.rtf (5.06 KB)
Well WireGuard server did not show any connection established. Probably it would be necessary to perform some package tracings on the router to so if there is some communication between client and server. Usually it’s possible to identify the WireGuard packages
Connection is not active for long. It get disconnected after a couple of second’s
2020-08-01 10:20:30.173455: [APP] Tunnel 'Odroid wg0-client.conf' connection status changed to 'connected'
2020-08-01 10:20:34.298061: [APP] Status update notification timeout for tunnel 'Odroid wg0-client.conf'. Tunnel status is now 'connected'.
2020-08-01 10:21:06.724452: [APP] startDeactivation: Tunnel: Odroid wg0-client.conf
2020-08-01 10:21:06.727976: [APP] Tunnel 'Odroid wg0-client.conf' connection status changed to 'disconnecting'
So,
I reinstalled Wireguard on its own.
Straight up vanilla install with the pre-written wg0-client.conf and the output for wg is the same
public key: ************************************************GUg=
private key: (hidden)
listening port: 51820
peer: *******************************************************+bB0=
allowed ips: 10.9.0.2/32
In fact, running wg returns the same even if the client isn’t running on my laptop.
In double fact, even after rebooting the server and running sudo wg I get exactly the same output as above with the client still not running on the laptop. Like there’s some phantom config left over from an earlier install or something?
The peer key above matches the public key of the wg0.conf file
Same thing after stopping and restarting Wireguard.
I’ve also just discovered that the client connection remains active even after the client app is quit.
Update to the update:
So, I configured it on my phone this time using the QR code printed to the screen, so it’s using wg0-client.conf and when running sudo wg it returns
root@HC1:/home/jon# wg
interface: wg0
public key: ***************************************************GUg=
private key: (hidden)
listening port: 51820
peer: ********************************************************+bB0=
endpoint: 192.168.20.1:59283
allowed ips: 10.9.0.2/32
latest handshake: 3 seconds ago
transfer: 9.60 KiB received, 16.18 KiB sent
but… I can’t access my nextcloud instance on the phone and my public ip remains the same as when not connected to the VPN
Okay we’re one step further. How did you add the config before when not using the QR code? Copying public and private key files manually around sounds not very handy  .
.
Okay please assure that on the phone AllowedIPs: 0.0.0.0/0, ::/0 is set so that all requests are forced through the tunnel.
Also a check is if http://www.whatsmydnsserver.com/ used on the phone reports the DNS configured in the wg0-client.conf instead of the mobile network provider DNS.
On the server, iptables forwarding rules have been established correctly?
iptables -L
iptables6 -L
and sysctl allows it as well?
sysctl net.ipv4.conf.wg0.forwarding net.ipv4.conf.$(mawk 'NR==3' /run/dietpi/.network).forwarding
sysctl net.ipv6.conf.$(mawk 'NR==3' /run/dietpi/.network).accept_ra
sysctl net.ipv6.conf.wg0.forwarding net.ipv6.conf.$(mawk 'NR==3' /run/dietpi/.network).forwarding
I found an iPhone SE somewhere on my home office and was testing WireGuard without issues. Pls can you post both, WireGuard server as well as client config files. And I would recommend to test VPN from outside your local network. (eg. use mobile internet on your mobile phone)
MichaIng Previously I was trying to configure my laptop, which was the machine I was using to ssh to the server, so I was just copying and pasting the config files between the two.
Neither my laptop (not connected to VPN) nor my phone (either when connected to the vpn or not) had a result returned by
whatsmydnsserver.com. The gears gif is still spinning away on my laptop trying to figure it out.
In fact, there was no internet access at all on the phone when the VPN was on, regardless of whether I was connected to my wifi network or using cellular data.
Wireguard seems to be horribly broken or there’s something deeply amiss somewhere else.
**** server seems to be hung on iptables -L ***
5 minutes now and no response from that command
Okay if server hangs on iptables -L then your issues are at a different level, since this independent from WireGuard  .
.
Have you checked dmesg for kernel errors or upgraded the kernel to latest version: apt update && apt full-upgrade