Creating a bug report/issue
Required Information
-
DietPi version |
cat /boot/dietpi/.version
G_DIETPI_VERSION_CORE=8
G_DIETPI_VERSION_SUB=13
G_DIETPI_VERSION_RC=2
G_GITBRANCH=‘master’
G_GITOWNER=‘MichaIng’
G_LIVE_PATCH_STATUS[0]=‘applied’
G_LIVE_PATCH_STATUS[1]=‘not applicable’ -
Distro version |
echo $G_DISTRO_NAME $G_RASPBIAN
bullseye -
Kernel version |
uname -a
Linux DietPi 5.10.0-21-amd64 #1 SMP Debian 5.10.162-1 (2023-01-21) x86_64 GNU/Linux -
SBC model |
echo $G_HW_MODEL_NAMEor (EG: RPi3)
Native PC (x86_64) -
Power supply used | (EG: 5V 1A RAVpower)
Dell 90w PSU -
SD card used | (EG: SanDisk ultra)
PCIe SSD
Additional Information (if applicable)
-
Software title | (EG: Nextcloud)
Nextcloud -
Was the software title installed freshly or updated/migrated?
Fresh install, has been updated several increments -
Can this issue be replicated on a fresh installation of DietPi
Have not tried
← If you sent a “dietpi-bugreport”, please paste the ID here →
- Bug report ID |
echo $G_HW_UUID
Steps to reproduce
- Restrict general root directory access (require all denied) in Apache config, opening (require all granted) only directories with running services. I have Nextcloud and PiHole configured on this server, both are served from different directories.
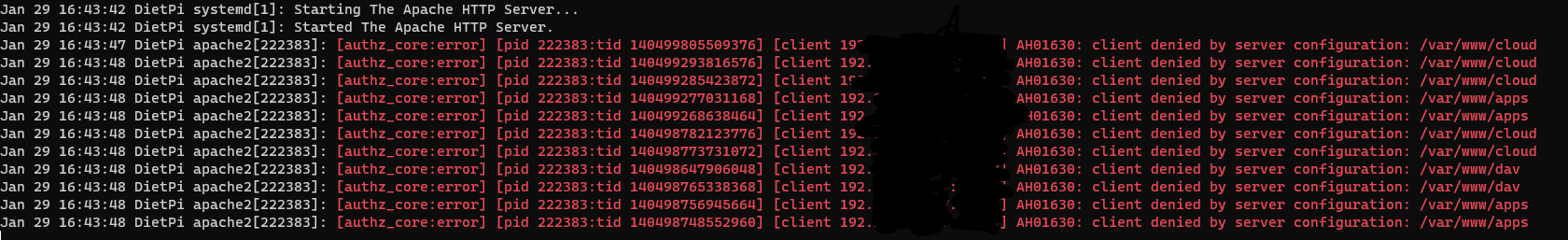
- journalctl -f -n 75
- See tons of 403 errors where my internal IPs are getting denied from certain Nextcloud directories that do not exist. E.G. [authz_core:error] [pid 222383:tid 140497423161088] [client X.X.X.X:55662] AH01630: client denied by server configuration: /var/www/dav
These 403 errors are initiated when opening the Nextloud desktop, web, and Android clients, where Nextcloud is calling on these diretories.
Expected behaviour
No Apache errors for unauthorized directories that also do not exist
- …
Actual behaviour
Apache errors for unauthorized directories that also do not exist
- …
Extra details
Note that the clients still seem to function OK, with the usual occasional Nextcloud hiccups. Syncing and other things seem to work just fine.
directory paths that are 403’d:
/var/www/apps
/var/www/cloud
/var/www/dav
/var/www/204
/var/www/avatar
etc…
Output of my main Apache config:
<Directory />
Options FollowSymLinks
AllowOverride None
Require all denied
</Directory>
<Directory /usr/share>
AllowOverride None
Require all granted
</Directory>
<Directory /var/www/nextcloud>
Options Indexes FollowSymLinks
AllowOverride None
Require all granted
</Directory>
<Directory /var/www/admin>
Options Indexes FollowSymLinks
AllowOverride None
Require all granted
</Directory>
<Directory /var/www/html/admin>
Options Indexes FollowSymLinks
AllowOverride None
Require all granted
</Directory>
Potentially related issue (but no actual resolution to my specific problem) on Github: AH01630: client denied by server configuration: /var/www/nextcloud/config · Issue #15688 · nextcloud/server · GitHub