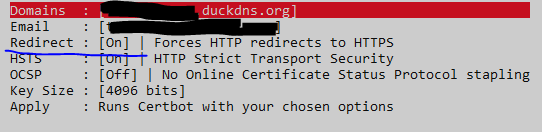
Hi there,
For some reason, I cannot renew my certificates:
Not sure if it has anything to do with https. Creating the certificates worked, just renewal doesn’t…
root@DietPi:~# certbot renew
Saving debug log to /var/log/letsencrypt/letsencrypt.log
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Processing /etc/letsencrypt/renewal/mydomain.org.conf
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Cert is due for renewal, auto-renewing...
Plugins selected: Authenticator webroot, Installer None
Renewing an existing certificate for mydomain.org
Performing the following challenges:
http-01 challenge for mydomain.org
Using the webroot path /var/www for all unmatched domains.
Waiting for verification...
Challenge failed for domain mydomain.org
http-01 challenge for mydomain.org
Cleaning up challenges
Failed to renew certificate mydomain.org with error: Some challenges have failed.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
All renewals failed. The following certificates could not be renewed:
/etc/letsencrypt/live/mydomain.org/fullchain.pem (failure)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1 renew failure(s), 0 parse failure(s)
IMPORTANT NOTES:
- The following errors were reported by the server:
Domain: theavengers.duckdns.org
Type: connection
Detail: MyIP: Fetching
https://mydomain.org/.well-known/acme-challenge/-QBfYioEZMT76lK6auXUamar--zBpT6RjfCuaW0GstA:
Error getting validation data
To fix these errors, please make sure that your domain name was
entered correctly and the DNS A/AAAA record(s) for that domain
contain(s) the right IP address. Additionally, please check that
your computer has a publicly routable IP address and that no
firewalls are preventing the server from communicating with the
client. If you're using the webroot plugin, you should also verify
that you are serving files from the webroot path you provided.
Log says:
root@DietPi:~# cat /var/log/letsencrypt/letsencrypt.log
2023-02-06 12:29:56,349:DEBUG:certbot._internal.main:certbot version: 1.12.0
2023-02-06 12:29:56,352:DEBUG:certbot._internal.main:Location of certbot entry point: /usr/bin/certbot
2023-02-06 12:29:56,353:DEBUG:certbot._internal.main:Arguments: []
2023-02-06 12:29:56,354:DEBUG:certbot._internal.main:Discovered plugins: PluginsRegistry(PluginEntryPoint#manual,PluginEntryPoint#null,PluginEntryPoint#standalone,PluginEntryPoint#webroot)
2023-02-06 12:29:57,282:DEBUG:certbot._internal.log:Root logging level set at 20
2023-02-06 12:29:57,284:INFO:certbot._internal.log:Saving debug log to /var/log/letsencrypt/letsencrypt.log
2023-02-06 12:29:57,377:DEBUG:certbot.display.util:Notifying user: Processing /etc/letsencrypt/renewal/mydomain.org.conf
2023-02-06 12:29:57,552:DEBUG:certbot._internal.plugins.selection:Requested authenticator <certbot._internal.cli.cli_utils._Default object at 0x7550a0d0> and installer <certbot._internal.cli.cli_utils._Default object at 0x7550a0d0>
2023-02-06 12:29:58,687:DEBUG:urllib3.connectionpool:Starting new HTTP connection (1): r3.o.lencr.org:80
2023-02-06 12:29:58,885:DEBUG:urllib3.connectionpool:http://r3.o.lencr.org:80 "POST / HTTP/1.1" 200 503
2023-02-06 12:29:58,895:DEBUG:certbot.ocsp:OCSP response for certificate /etc/letsencrypt/archive/mydomain.org/cert2.pem is signed by the certificate's issuer.
2023-02-06 12:29:59,004:DEBUG:certbot.ocsp:OCSP certificate status for /etc/letsencrypt/archive/mydomain.org/cert2.pem is: OCSPCertStatus.GOOD
2023-02-06 12:29:59,039:DEBUG:certbot._internal.storage:Should renew, less than 30 days before certificate expiry 2023-02-25 20:41:14 UTC.
2023-02-06 12:29:59,040:INFO:certbot._internal.renewal:Cert is due for renewal, auto-renewing...
2023-02-06 12:29:59,041:DEBUG:certbot._internal.plugins.selection:Requested authenticator webroot and installer None
2023-02-06 12:29:59,043:DEBUG:certbot._internal.plugins.selection:Single candidate plugin: * webroot
Description: Place files in webroot directory
Interfaces: IAuthenticator, IPlugin
Entry point: webroot = certbot._internal.plugins.webroot:Authenticator
Initialized: <certbot._internal.plugins.webroot.Authenticator object at 0x754aae20>Prep: True
2023-02-06 12:29:59,045:DEBUG:certbot._internal.plugins.selection:Selected authenticator <certbot._internal.plugins.webroot.Authenticator object at 0x754aae20> and installer None
2023-02-06 12:29:59,046:INFO:certbot._internal.plugins.selection:Plugins selected: Authenticator webroot, Installer None
2023-02-06 12:29:59,869:DEBUG:certbot._internal.main:Picked account: <Account(RegistrationResource(body=Registration(key=None, contact=(), agreement=None, status=None, terms_of_service_agreed=None, only_return_existing=None, external_account_binding=None), uri='https://acme-v02.api.letsencrypt.org/acme/acct/811133197', new_authzr_uri=None, terms_of_service=None), 88bfdb69be896aa7f9741936db1232f4, Meta(creation_dt=datetime.datetime(2022, 11, 6, 8, 27, 19, tzinfo=<UTC>), creation_host='DietPi', register_to_eff=None))>
2023-02-06 12:29:59,873:DEBUG:acme.client:Sending GET request to https://acme-v02.api.letsencrypt.org/directory.
2023-02-06 12:29:59,892:DEBUG:urllib3.connectionpool:Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org:443
2023-02-06 12:30:00,389:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "GET /directory HTTP/1.1" 200 756
2023-02-06 12:30:00,391:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Mon, 06 Feb 2023 11:30:00 GMT
Content-Type: application/json
Content-Length: 756
Connection: keep-alive
Cache-Control: public, max-age=0, no-cache
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"keyChange": "https://acme-v02.api.letsencrypt.org/acme/key-change",
"meta": {
"caaIdentities": [
"letsencrypt.org"
],
"termsOfService": "https://letsencrypt.org/documents/LE-SA-v1.3-September-21-2022.pdf",
"website": "https://letsencrypt.org"
},
"newAccount": "https://acme-v02.api.letsencrypt.org/acme/new-acct",
"newNonce": "https://acme-v02.api.letsencrypt.org/acme/new-nonce",
"newOrder": "https://acme-v02.api.letsencrypt.org/acme/new-order",
"renewalInfo": "https://acme-v02.api.letsencrypt.org/get/draft-ietf-acme-ari-00/renewalInfo/",
"revokeCert": "https://acme-v02.api.letsencrypt.org/acme/revoke-cert",
"t93J8W7ugfg": "https://community.letsencrypt.org/t/adding-random-entries-to-the-directory/33417"
}
2023-02-06 12:30:00,422:DEBUG:certbot.display.util:Notifying user: Renewing an existing certificate for mydomain.org
2023-02-06 12:30:11,796:DEBUG:certbot.crypto_util:Generating RSA key (4096 bits): /etc/letsencrypt/keys/0020_key-certbot.pem
2023-02-06 12:30:12,084:DEBUG:certbot.crypto_util:Creating CSR: /etc/letsencrypt/csr/0020_csr-certbot.pem
2023-02-06 12:30:12,090:DEBUG:acme.client:Requesting fresh nonce
2023-02-06 12:30:12,091:DEBUG:acme.client:Sending HEAD request to https://acme-v02.api.letsencrypt.org/acme/new-nonce.
2023-02-06 12:30:12,265:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "HEAD /acme/new-nonce HTTP/1.1" 200 0
2023-02-06 12:30:12,268:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Mon, 06 Feb 2023 11:30:11 GMT
Connection: keep-alive
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: F977ImihL7t5Gtn-oQjO5COWlubzcymM4i87C3lv2nYIY-Y
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
2023-02-06 12:30:12,270:DEBUG:acme.client:Storing nonce: F977ImihL7t5Gtn-oQjO5COWlubzcymM4i87C3lv2nYIY-Y
2023-02-06 12:30:12,271:DEBUG:acme.client:JWS payload:
b'{\n "identifiers": [\n {\n "type": "dns",\n "value": "mydomain.org"\n }\n ]\n}'
2023-02-06 12:30:12,395:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/new-order:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvODExMTMzMTk3IiwgIm5vbmNlIjogIkY5NzdJbWloTDd0NUd0bi1vUWpPNUNPV2x1YnpjeW1NNGk4N0MzbHYybllJWS1ZIiwgInVybCI6ICJodHRwczovL2FjbWUtdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9uZXctb3JkZXIifQ",
"signature": "1bm0DwfzQYtAQRXXmj3xUWYMRGeN39j_OM2sYkmAantJnbGIDo4ensWAtv4GBkvquL_oh6x2sVi3NOuD5AwRLJ6BQki7g1OCz5W-jEdm7FV3a96F9UvBGTTdmW98sA26Hyg6b-kuPIceaodGCnR1tgvd2djJqEVYvo_maNW8xfadOmgddbE9bBscGyRWkVJKDpJ839TmcgRa6-_5VhsKr7hnRv9jjKajNDhYmcM4vMU1Em36QuTSkQmVJ-EEpogGOxTDgNP27kEDFL0QmsP6DYm3bkyi81KllxarUYNTtwBuTWB68i0qI4ROHQKWTRLX1XUyLMbRRFLo_PqUYqX079Rg0invDcTKqjDsnBKDlIDqY1SuELGgWMDKsvZKuX0qRSH43aNwxeUiRwxSwJ6-KsJTyUS9D-lX315oA-7NxrEqircKN9bVpT50IXy5uSd0HkSxGWOs2WR6pmUsc7XnQcyZAapeHS0ifU7oZtwW-YO7kBOPNglY8IU1wwGGnuwX2yP70MwehOacxYUaxpvSa-Cb2x_40rxL-uFyz7Xzqu5TsyO9RkOtW_I5IlsKU8bfVqGRcPd9w21dh1LeJFcAGHv4Mpa2MgtmAp0CyzQba8nEqDgB8OrgpE29hJLfL8PB_sGw0CjqqXAvKPhOIzbgkAOZnwJ4hlJCqH-TIh_8apM",
"payload": "ewogICJpZGVudGlmaWVycyI6IFsKICAgIHsKICAgICAgInR5cGUiOiAiZG5zIiwKICAgICAgInZhbHVlIjogInRoZWF2ZW5nZXJzLmR1Y2tkbnMub3JnIgogICAgfQogIF0KfQ"
}
2023-02-06 12:30:12,590:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/new-order HTTP/1.1" 201 348
2023-02-06 12:30:12,594:DEBUG:acme.client:Received response:
HTTP 201
Server: nginx
Date: Mon, 06 Feb 2023 11:30:12 GMT
Content-Type: application/json
Content-Length: 348
Connection: keep-alive
Boulder-Requester: 811133197
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Location: https://acme-v02.api.letsencrypt.org/acme/order/811133197/163218900496
Replay-Nonce: F977Z0sk1_NV3aZfq9T2P9m4GXiBsEJkHXPtRxuQmZaPCLk
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"status": "pending",
"expires": "2023-02-13T11:30:12Z",
"identifiers": [
{
"type": "dns",
"value": "mydomain.org"
}
],
"authorizations": [
"https://acme-v02.api.letsencrypt.org/acme/authz-v3/201291288256"
],
"finalize": "https://acme-v02.api.letsencrypt.org/acme/finalize/811133197/163218900496"
}
2023-02-06 12:30:12,595:DEBUG:acme.client:Storing nonce: F977Z0sk1_NV3aZfq9T2P9m4GXiBsEJkHXPtRxuQmZaPCLk
2023-02-06 12:30:12,597:DEBUG:acme.client:JWS payload:
b''
2023-02-06 12:30:12,716:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/201291288256:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvODExMTMzMTk3IiwgIm5vbmNlIjogIkY5NzdaMHNrMV9OVjNhWmZxOVQyUDltNEdYaUJzRUprSFhQdFJ4dVFtWmFQQ0xrIiwgInVybCI6ICJodHRwczovL2FjbWUtdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9hdXRoei12My8yMDEyOTEyODgyNTYifQ",
"signature": "eNLg9wBen0MEsYMRKlDTEP6rtzUR6TXAx7pW9HjveAj-WRY-72Xz2OmRhY5rL74Gp_PUUVLb0jZU36D_KW_pPuz_3wrAfs2gJTMk08u2h6kyUFAesYAT-sQfTKHWAV7jb0RqeZKGzAbXBI_plu0jbCynPKykh5Pl41VBARVRxbH3eGuq0M_HnJIaIYwjdMAri6J5SrH6hvN6Tu9dKaTKRWD8zT-DE654P_4hUeOPH_w5z42CJP2ysVICPm-Ragh9zZ6s2-M_PsrW7HPbT98n7H4824KZvdVgUABOcxzUwZVSDNlt7IB8TW-avcouKdpivyMLkRhpmg2mRhUnJT2y97AviWIl0fAa-AxSL0bQeiaDOnHUXecviQbDBMgwQelbgF_ZCbH6b3jIa3vgCt6fQ2c1f1JUp0XGahLVlMs0sv8pWUARpxAW6TsgDncsI6EqjjW3TN7aAs5vAFZm7seMvcI2lG2GX8PEv5uI_U7vErZjqhGGT095r64oAYDbYvuz3Xsrv_2gHRDLdKNV1V_Nx4OxbdmkcMnTeRHabdqOTak4ESq5EJDhVKS63Rqn59ezwIyPPgF_-_qpO3kymgCvnHVrZX1mq4X2JNmEwE1CcXSg81Iy4VVefl6YkPL--QmhHmhmzuF172LAPJ6f8_whVCTbYzxv-8CoVi_r9F4i8Yo",
"payload": ""
}
2023-02-06 12:30:12,890:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz-v3/201291288256 HTTP/1.1" 200 807
2023-02-06 12:30:12,894:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Mon, 06 Feb 2023 11:30:12 GMT
Content-Type: application/json
Content-Length: 807
Connection: keep-alive
Boulder-Requester: 811133197
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: 2712OfSyhyycW-dkRNmnnneh4w-EywvRuBHkBfUCny3CEjw
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "mydomain.org"
},
"status": "pending",
"expires": "2023-02-13T11:30:12Z",
"challenges": [
{
"type": "http-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/201291288256/eh-lzg",
"token": "xclDxBCplrSQSNvv9klstrMm16SUjsf7ekMkTU6RldE"
},
{
"type": "dns-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/201291288256/eGcdpA",
"token": "xclDxBCplrSQSNvv9klstrMm16SUjsf7ekMkTU6RldE"
},
{
"type": "tls-alpn-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/201291288256/WYpL1Q",
"token": "xclDxBCplrSQSNvv9klstrMm16SUjsf7ekMkTU6RldE"
}
]
}
2023-02-06 12:30:12,895:DEBUG:acme.client:Storing nonce: 2712OfSyhyycW-dkRNmnnneh4w-EywvRuBHkBfUCny3CEjw
2023-02-06 12:30:12,899:INFO:certbot._internal.auth_handler:Performing the following challenges:
2023-02-06 12:30:12,900:INFO:certbot._internal.auth_handler:http-01 challenge for mydomain.org
2023-02-06 12:30:12,902:INFO:certbot._internal.plugins.webroot:Using the webroot path /var/www for all unmatched domains.
2023-02-06 12:30:12,904:DEBUG:certbot._internal.plugins.webroot:Creating root challenges validation dir at /var/www/.well-known/acme-challenge
2023-02-06 12:30:13,242:DEBUG:certbot._internal.plugins.webroot:Attempting to save validation to /var/www/.well-known/acme-challenge/xclDxBCplrSQSNvv9klstrMm16SUjsf7ekMkTU6RldE
2023-02-06 12:30:13,245:INFO:certbot._internal.auth_handler:Waiting for verification...
2023-02-06 12:30:13,247:DEBUG:acme.client:JWS payload:
b'{}'
2023-02-06 12:30:13,374:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/chall-v3/201291288256/eh-lzg:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvODExMTMzMTk3IiwgIm5vbmNlIjogIjI3MTJPZlN5aHl5Y1ctZGtSTm1ubm5laDR3LUV5d3ZSdUJIa0JmVUNueTNDRWp3IiwgInVybCI6ICJodHRwczovL2FjbWUtdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9jaGFsbC12My8yMDEyOTEyODgyNTYvZWgtbHpnIn0",
"signature": "rdeiz6Ts8e9M_ny7jcbH2cLblSlYiS-LxIc1-kbUxkm3Fc_cxOehZo37rLisdwj7llacLcPowqwUeqQPOv5YB6ROyddV1dH1CuV-AxzD0q__2JVxkvX-ABhOUHLUbcOkdDpkpK59AI5HicBcmgs9deO1Kb8hE71lWFIWsBjpCGS_ECw-zUCettrkecXd3w6KPanRoJqJgPY61UM3sBaisOSNkC4oRvdQ8qqBS5gR1ZYv3kq3PqXJxwf1DuWgPKyGge7Yd-8iXwOrazI6Rd6SDzOzxmjDWcHd7hLvyIxZODekGNlHPNPDoTkl7YZqvnu91IjrKxLRqiOBaMSyP57tlxOrgPpiNtsAswC1DplaWUHM7OIcuzC0GtMT_oHA0HkNxnlyFsE-yQitTjmtByGTjtWsd0QyKl8ng3nlDwRQSe_dzY2STIyQnbWfXxm-_iAMUgALwqBN9GQ60agd7XZmWYvYtSwp-q5eEtEjyBYAtlY5Uh9EEuVXKUXdIyWm16g2zm8B0vqywGRzmi8zTjRET4B0vdT7vKyzpYtjrcxsWdPpnZk4VcY3PyU-Vz3QGsrt0x12baFqIQV6BnI1OKy7LvNcmlt0FY_aF572nTyTHrvbIkoAcMeY7d8KZd4cXravQJFYX7yWVC2NSKgpct592ruHJBZuOYrjr1eeSYiz8qM",
"payload": "e30"
}
2023-02-06 12:30:13,560:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/chall-v3/201291288256/eh-lzg HTTP/1.1" 200 187
2023-02-06 12:30:13,564:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Mon, 06 Feb 2023 11:30:13 GMT
Content-Type: application/json
Content-Length: 187
Connection: keep-alive
Boulder-Requester: 811133197
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index", <https://acme-v02.api.letsencrypt.org/acme/authz-v3/201291288256>;rel="up"
Location: https://acme-v02.api.letsencrypt.org/acme/chall-v3/201291288256/eh-lzg
Replay-Nonce: F9772sd5a2ZsEht9JSakOagBID32WKDugbBI29SSPnHM3cg
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"type": "http-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/201291288256/eh-lzg",
"token": "xclDxBCplrSQSNvv9klstrMm16SUjsf7ekMkTU6RldE"
}
2023-02-06 12:30:13,565:DEBUG:acme.client:Storing nonce: F9772sd5a2ZsEht9JSakOagBID32WKDugbBI29SSPnHM3cg
2023-02-06 12:30:14,569:DEBUG:acme.client:JWS payload:
b''
2023-02-06 12:30:14,696:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/201291288256:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvODExMTMzMTk3IiwgIm5vbmNlIjogIkY5Nzcyc2Q1YTJac0VodDlKU2FrT2FnQklEMzJXS0R1Z2JCSTI5U1NQbkhNM2NnIiwgInVybCI6ICJodHRwczovL2FjbWUtdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9hdXRoei12My8yMDEyOTEyODgyNTYifQ",
"signature": "i1btPVvWcCunJPZGLO1_cR2Y0h0LhbGjhgWPZYr-yGyjOgSgmqpRNxzhFaRUGD2wRK5pY_lwbJw6TqcvSC_v4kuaKBnB2uUuGcPFSrbqJwpQZyQxhkas1DfPlzcBYoLg9t5uzfFGBXjUGglx0Ivmx_GpXo46Cb-Reboc4Tr6Up27TXrF0tymUZn5Ym5L5KQfIvlzpJTQsTSVKOsL4U8JNVxWIr1ElQLYHWp3XRkZ3xHVwLpbBbhJN41d2aVusi7cbdoKW2kOZuRvqaePpo7UmpmvFtgJdv1I9CeyanhY6onb5RxdL63La5q7evYG-XSHfcWyTg7OD3gxeHA1JtSrb4ZQEWazyt0iAQowpf9gyRPlgtNjtukKHGgPbF_ARzjdQmp_lWs6zbQsrjsDGEofOTpc0Gxvls3LKlE24PtPjhGc7onU6sQzsTNKTDJySsu0k0Wvo3mSBc-XI5tYGaep_rCCAbW5-6vR1Nc1fuMTRPGLPIFksCF760f2jWpDM7aUHuplzl5kaWeSWX5zwTTiLBZEMdR7EZUsadCcvL5yejhkPatAj1TvE38jQh6L0dutTHo6UjgiFY8UEepcN2apRWNIp9hHQr8xxZghP45JZwjftS2lwR2jhMDWQuSpfmGUbVHyFcIG2S-Thzd1sRNJzV4uCIRqjs8AOutzcZXHeJY",
"payload": ""
}
2023-02-06 12:30:14,876:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz-v3/201291288256 HTTP/1.1" 200 1948
2023-02-06 12:30:14,880:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Mon, 06 Feb 2023 11:30:14 GMT
Content-Type: application/json
Content-Length: 1948
Connection: keep-alive
Boulder-Requester: 811133197
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: F977stlyy8o7Q-xyLazojX3KWX3EicchO8E9hHR_oxHeSrk
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "mydomain.org"
},
"status": "invalid",
"expires": "2023-02-13T11:30:12Z",
"challenges": [
{
"type": "http-01",
"status": "invalid",
"error": {
"type": "urn:ietf:params:acme:error:connection",
"detail": "MyIP: Fetching https://mydomain.org/.well-known/acme-challenge/xclDxBCplrSQSNvv9klstrMm16SUjsf7ekMkTU6RldE: Error getting validation data",
"status": 400
},
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/201291288256/eh-lzg",
"token": "xclDxBCplrSQSNvv9klstrMm16SUjsf7ekMkTU6RldE",
"validationRecord": [
{
"url": "http://mydomain.org/.well-known/acme-challenge/xclDxBCplrSQSNvv9klstrMm16SUjsf7ekMkTU6RldE",
"hostname": "mydomain.org",
"port": "80",
"addressesResolved": [
"MyIP",
"MyIPV6"
],
"addressUsed": "MyIPV6"
},
{
"url": "http://mydomain.org/.well-known/acme-challenge/xclDxBCplrSQSNvv9klstrMm16SUjsf7ekMkTU6RldE",
"hostname": "mydomain.org",
"port": "80",
"addressesResolved": [
"MyIP",
"MyIPV6"
],
"addressUsed": "MyIP"
},
{
"url": "https://mydomain.org/.well-known/acme-challenge/xclDxBCplrSQSNvv9klstrMm16SUjsf7ekMkTU6RldE",
"hostname": "mydomain.org",
"port": "443",
"addressesResolved": [
"MyIP",
"MyIPV6"
],
"addressUsed": "MyIPV6"
}
],
"validated": "2023-02-06T11:30:13Z"
}
]
}
2023-02-06 12:30:14,881:DEBUG:acme.client:Storing nonce: F977stlyy8o7Q-xyLazojX3KWX3EicchO8E9hHR_oxHeSrk
2023-02-06 12:30:14,884:WARNING:certbot._internal.auth_handler:Challenge failed for domain mydomain.org
2023-02-06 12:30:14,885:INFO:certbot._internal.auth_handler:http-01 challenge for mydomain.org
2023-02-06 12:30:14,887:DEBUG:certbot._internal.reporter:Reporting to user: The following errors were reported by the server:
Domain: mydomain.org
Type: connection
Detail: MyIP: Fetching https://mydomain.org/.well-known/acme-challenge/xclDxBCplrSQSNvv9klstrMm16SUjsf7ekMkTU6RldE: Error getting validation data
To fix these errors, please make sure that your domain name was entered correctly and the DNS A/AAAA record(s) for that domain contain(s) the right IP address. Additionally, please check that your computer has a publicly routable IP address and that no firewalls are preventing the server from communicating with the client. If you're using the webroot plugin, you should also verify that you are serving files from the webroot path you provided.
2023-02-06 12:30:14,935:DEBUG:certbot._internal.error_handler:Encountered exception:
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/certbot/_internal/auth_handler.py", line 91, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/usr/lib/python3/dist-packages/certbot/_internal/auth_handler.py", line 180, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
certbot.errors.AuthorizationError: Some challenges have failed.
2023-02-06 12:30:14,936:DEBUG:certbot._internal.error_handler:Calling registered functions
2023-02-06 12:30:14,937:INFO:certbot._internal.auth_handler:Cleaning up challenges
2023-02-06 12:30:14,938:DEBUG:certbot._internal.plugins.webroot:Removing /var/www/.well-known/acme-challenge/xclDxBCplrSQSNvv9klstrMm16SUjsf7ekMkTU6RldE
2023-02-06 12:30:14,941:DEBUG:certbot._internal.plugins.webroot:All challenges cleaned up
2023-02-06 12:30:14,945:ERROR:certbot._internal.renewal:Failed to renew certificate mydomain.org with error: Some challenges have failed.
2023-02-06 12:30:14,967:DEBUG:certbot._internal.renewal:Traceback was:
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/certbot/_internal/renewal.py", line 485, in handle_renewal_request
main.renew_cert(lineage_config, plugins, renewal_candidate)
File "/usr/lib/python3/dist-packages/certbot/_internal/main.py", line 1234, in renew_cert
renewed_lineage = _get_and_save_cert(le_client, config, lineage=lineage)
File "/usr/lib/python3/dist-packages/certbot/_internal/main.py", line 123, in _get_and_save_cert
renewal.renew_cert(config, domains, le_client, lineage)
File "/usr/lib/python3/dist-packages/certbot/_internal/renewal.py", line 345, in renew_cert
new_cert, new_chain, new_key, _ = le_client.obtain_certificate(domains, new_key)
File "/usr/lib/python3/dist-packages/certbot/_internal/client.py", line 374, in obtain_certificate
orderr = self._get_order_and_authorizations(csr.data, self.config.allow_subset_of_names)
File "/usr/lib/python3/dist-packages/certbot/_internal/client.py", line 421, in _get_order_and_authorizations
authzr = self.auth_handler.handle_authorizations(orderr, best_effort)
File "/usr/lib/python3/dist-packages/certbot/_internal/auth_handler.py", line 91, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/usr/lib/python3/dist-packages/certbot/_internal/auth_handler.py", line 180, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
certbot.errors.AuthorizationError: Some challenges have failed.
2023-02-06 12:30:14,968:DEBUG:certbot.display.util:Notifying user:
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
2023-02-06 12:30:14,969:ERROR:certbot._internal.renewal:All renewals failed. The following certificates could not be renewed:
2023-02-06 12:30:14,970:ERROR:certbot._internal.renewal: /etc/letsencrypt/live/mydomain.org/fullchain.pem (failure)
2023-02-06 12:30:14,971:DEBUG:certbot.display.util:Notifying user: - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
2023-02-06 12:30:14,972:DEBUG:certbot._internal.log:Exiting abnormally:
Traceback (most recent call last):
File "/usr/bin/certbot", line 33, in <module>
sys.exit(load_entry_point('certbot==1.12.0', 'console_scripts', 'certbot')())
File "/usr/lib/python3/dist-packages/certbot/main.py", line 15, in main
return internal_main.main(cli_args)
File "/usr/lib/python3/dist-packages/certbot/_internal/main.py", line 1413, in main
return config.func(config, plugins)
File "/usr/lib/python3/dist-packages/certbot/_internal/main.py", line 1317, in renew
renewal.handle_renewal_request(config)
File "/usr/lib/python3/dist-packages/certbot/_internal/renewal.py", line 510, in handle_renewal_request
raise errors.Error("{0} renew failure(s), {1} parse failure(s)".format(
certbot.errors.Error: 1 renew failure(s), 0 parse failure(s)
2023-02-06 12:30:15,026:ERROR:certbot._internal.log:1 renew failure(s), 0 parse failure(s)
root@DietPi:~#
Any idea?
Thanks
t