Creating a bug report/issue
Required Information
- DietPi version |
G_DIETPI_VERSION_CORE=8 G_DIETPI_VERSION_SUB=15 G_DIETPI_VERSION_RC=2 G_GITBRANCH='master' G_GITOWNER='MichaIng' G_LIVE_PATCH_STATUS[0]='not applicable' - Distro version |
bullseye - Kernel version |
Linux DietPi 5.15.93-rockchip64 #23.02.2 SMP PREEMPT Fri Feb 17 23:48:36 UTC 2023 aarch64 GNU/Linux - SBC model |
ROCKPro64 (aarch64)
Additional Information (if applicable)
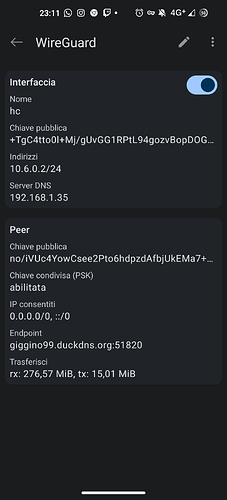
- Software title | Dietpi-Vpn
Once connected to ProtonVPn’s free vpn the traffic stays at 0 and when I try to do a speedtest it works but stays with my ip so it’s not working … and the kill switch doesn’t work either
to connect via dietpi-vpn I had to install openvpn
I want to say that in any case I have wireguard with pivpn to connect remotely
root@DietPi:~# route -v
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default nameserver 0.0.0.0 UG 0 0 0 eth0
10.6.0.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
10.8.0.0 10.8.0.2 255.255.255.0 UG 0 0 0 tun0
10.8.0.2 0.0.0.0 255.255.255.255 UH 0 0 0 tun0
172.17.0.0 0.0.0.0 255.255.0.0 U 0 0 0 docker0
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
root@DietPi:~# sudo ip route show table all
default via 192.168.1.1 dev eth0 onlink
10.6.0.0/24 dev wg0 proto kernel scope link src 10.6.0.1
10.8.0.0/24 via 10.8.0.2 dev tun0
10.8.0.2 dev tun0 proto kernel scope link src 10.8.0.1
172.17.0.0/16 dev docker0 proto kernel scope link src 172.17.0.1
192.168.1.0/24 dev eth0 proto kernel scope link src 192.168.1.35
local 10.6.0.1 dev wg0 table local proto kernel scope host src 10.6.0.1
broadcast 10.6.0.255 dev wg0 table local proto kernel scope link src 10.6.0.1
local 10.8.0.1 dev tun0 table local proto kernel scope host src 10.8.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
local 172.17.0.1 dev docker0 table local proto kernel scope host src 172.17.0.1
broadcast 172.17.255.255 dev docker0 table local proto kernel scope link src 172.17.0.1
local 192.168.1.35 dev eth0 table local proto kernel scope host src 192.168.1.35
broadcast 192.168.1.255 dev eth0 table local proto kernel scope link src 192.168.1.35
::1 dev lo proto kernel metric 256 pref medium
fe80::/64 dev eth0 proto kernel metric 256 pref medium
fe80::/64 dev tun0 proto kernel metric 256 pref medium
fe80::/64 dev docker0 proto kernel metric 256 pref medium
fe80::/64 dev vetha797a1c proto kernel metric 256 pref medium
fe80::/64 dev vethd37561a proto kernel metric 256 pref medium
local ::1 dev lo table local proto kernel metric 0 pref medium
anycast fe80:: dev eth0 table local proto kernel metric 0 pref medium
anycast fe80:: dev tun0 table local proto kernel metric 0 pref medium
anycast fe80:: dev docker0 table local proto kernel metric 0 pref medium
anycast fe80:: dev vetha797a1c table local proto kernel metric 0 pref medium
anycast fe80:: dev vethd37561a table local proto kernel metric 0 pref medium
local fe80::42:72ff:fe3b:26a4 dev docker0 table local proto kernel metric 0 pref medium
local fe80::64f4:5dff:fee7:c10d dev vethd37561a table local proto kernel metric 0 pref medium
local fe80::99aa:91d0:1ffa:d45d dev tun0 table local proto kernel metric 0 pref medium
local fe80::ac59:7dff:fea3:d8d8 dev eth0 table local proto kernel metric 0 pref medium
local fe80::b8d4:d8ff:feba:9a1d dev vetha797a1c table local proto kernel metric 0 pref medium
multicast ff00::/8 dev eth0 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev tun0 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev wg0 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev docker0 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev vetha797a1c table local proto kernel metric 256 pref medium
multicast ff00::/8 dev vethd37561a table local proto kernel metric 256 pref medium
root@DietPi:~#