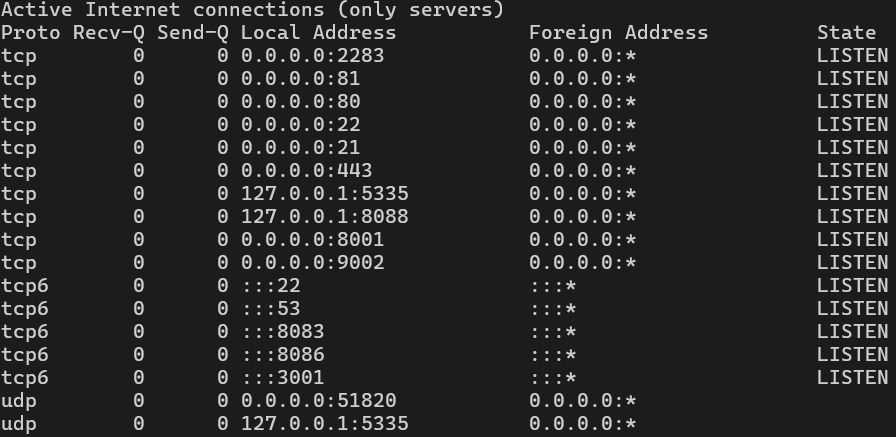
After upgrading my Wireguard VPN stopped working… it connects but doesnt have any internet… Im using AdguardHome with unbound and PiVPN
This is the handshake info…
[handshake]
10-23 11:13:22.471 22254 22336 D WireGuard/GoBackend/indaRaspberry: peer(aWxi…sDx8) - Handshake did not complete after 5 seconds, retrying (try 2)
10-23 11:13:22.471 22254 22336 D WireGuard/GoBackend/indaRaspberry: peer(aWxi…sDx8) - Sending handshake initiation
10-23 11:13:27.662 22254 22276 D WireGuard/GoBackend/indaRaspberry: peer(aWxi…sDx8) - Handshake did not complete after 5 seconds, retrying (try 2)
10-23 11:13:27.662 22254 22276 D WireGuard/GoBackend/indaRaspberry: peer(aWxi…sDx8) - Sending handshake initiation
[/handshake]
This is my wg0.conf… I had no iptables before and it was working after searching i decided to add the postup/postdown to see if that fixed the issue but it didnt…
[Interface]
PrivateKey = [pkey]
Address = 10.25.161.1/24
MTU = 1420
ListenPort = 51820
PostUp = iptables -w -t nat -A POSTROUTING -o eth0 -j MASQUERADE; ip6tables -w -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -w -t nat -D POSTROUTING -o eth0 -j MASQUERADE; ip6tables -w -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = [pkey]
PresharedKey = [prkey]
AllowedIPs = 10.25.161.2/32
This is my iptables-saves -c
# Generated by iptables-save v1.8.9 (nf_tables) on Wed Oct 23 16:22:01 2024
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:DOCKER - [0:0]
:DOCKER-ISOLATION-STAGE-1 - [0:0]
:DOCKER-ISOLATION-STAGE-2 - [0:0]
:DOCKER-USER - [0:0]
[17234:11503990] -A FORWARD -j DOCKER-USER
[17234:11503990] -A FORWARD -j DOCKER-ISOLATION-STAGE-1
[0:0] -A FORWARD -o docker0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
[0:0] -A FORWARD -o docker0 -j DOCKER
[0:0] -A FORWARD -i docker0 ! -o docker0 -j ACCEPT
[0:0] -A FORWARD -i docker0 -o docker0 -j ACCEPT
[20211:13119764] -A FORWARD -o br-d02055d3da93 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
[1350:70216] -A FORWARD -o br-d02055d3da93 -j DOCKER
[18032:8333293] -A FORWARD -i br-d02055d3da93 ! -o br-d02055d3da93 -j ACCEPT
[0:0] -A FORWARD -i br-d02055d3da93 -o br-d02055d3da93 -j ACCEPT
[0:0] -A DOCKER -d 172.17.0.2/32 ! -i docker0 -o docker0 -p tcp -m tcp --dport 9000 -j ACCEPT
[0:0] -A DOCKER -d 172.18.0.2/32 ! -i br-d02055d3da93 -o br-d02055d3da93 -p tcp -m tcp --dport 3001 -j ACCEPT
[0:0] -A DOCKER -d 172.18.0.5/32 ! -i br-d02055d3da93 -o br-d02055d3da93 -p tcp -m tcp --dport 80 -j ACCEPT
[0:0] -A DOCKER -d 172.18.0.5/32 ! -i br-d02055d3da93 -o br-d02055d3da93 -p tcp -m tcp --dport 81 -j ACCEPT
[513:26692] -A DOCKER -d 172.18.0.5/32 ! -i br-d02055d3da93 -o br-d02055d3da93 -p tcp -m tcp --dport 443 -j ACCEPT
[0:0] -A DOCKER-ISOLATION-STAGE-1 -i docker0 ! -o docker0 -j DOCKER-ISOLATION-STAGE-2
[7538:3742661] -A DOCKER-ISOLATION-STAGE-1 -i br-d02055d3da93 ! -o br-d02055d3da93 -j DOCKER-ISOLATION-STAGE-2
[17234:11503990] -A DOCKER-ISOLATION-STAGE-1 -j RETURN
[0:0] -A DOCKER-ISOLATION-STAGE-2 -o docker0 -j DROP
[0:0] -A DOCKER-ISOLATION-STAGE-2 -o br-d02055d3da93 -j DROP
[7538:3742661] -A DOCKER-ISOLATION-STAGE-2 -j RETURN
[39593:21523273] -A DOCKER-USER -j RETURN
COMMIT
# Completed on Wed Oct 23 16:22:01 2024
# Generated by iptables-save v1.8.9 (nf_tables) on Wed Oct 23 16:22:01 2024
*nat
:PREROUTING ACCEPT [59560:4405245]
:INPUT ACCEPT [59531:4403476]
:OUTPUT ACCEPT [109534:8212496]
:POSTROUTING ACCEPT [110884:8282712]
:DOCKER - [0:0]
[33513:2497081] -A PREROUTING -m addrtype --dst-type LOCAL -j DOCKER
[4:240] -A OUTPUT ! -d 127.0.0.0/8 -m addrtype --dst-type LOCAL -j DOCKER
[0:0] -A POSTROUTING -s 172.17.0.0/16 ! -o docker0 -j MASQUERADE
[29:1769] -A POSTROUTING -s 172.18.0.0/16 ! -o br-d02055d3da93 -j MASQUERADE
[0:0] -A POSTROUTING -s 10.25.161.0/24 -o eth0 -m comment --comment wireguard-nat-rule -j MASQUERADE
[0:0] -A POSTROUTING -s 172.17.0.2/32 -d 172.17.0.2/32 -p tcp -m tcp --dport 9000 -j MASQUERADE
[0:0] -A POSTROUTING -s 172.18.0.2/32 -d 172.18.0.2/32 -p tcp -m tcp --dport 3001 -j MASQUERADE
[0:0] -A POSTROUTING -s 172.18.0.5/32 -d 172.18.0.5/32 -p tcp -m tcp --dport 80 -j MASQUERADE
[0:0] -A POSTROUTING -s 172.18.0.5/32 -d 172.18.0.5/32 -p tcp -m tcp --dport 81 -j MASQUERADE
[0:0] -A POSTROUTING -s 172.18.0.5/32 -d 172.18.0.5/32 -p tcp -m tcp --dport 443 -j MASQUERADE
[0:0] -A DOCKER -i docker0 -j RETURN
[342:20520] -A DOCKER -i br-d02055d3da93 -j RETURN
[0:0] -A DOCKER ! -i docker0 -p tcp -m tcp --dport 9002 -j DNAT --to-destination 172.17.0.2:9000
[0:0] -A DOCKER ! -i br-d02055d3da93 -p tcp -m tcp --dport 2283 -j DNAT --to-destination 172.18.0.2:3001
[0:0] -A DOCKER ! -i br-d02055d3da93 -p tcp -m tcp --dport 80 -j DNAT --to-destination 172.18.0.5:80
[0:0] -A DOCKER ! -i br-d02055d3da93 -p tcp -m tcp --dport 81 -j DNAT --to-destination 172.18.0.5:81
[513:26692] -A DOCKER ! -i br-d02055d3da93 -p tcp -m tcp --dport 443 -j DNAT --to-destination 172.18.0.5:443
COMMIT
# Completed on Wed Oct 23 16:22:01 2024