-
DietPi version
G_DIETPI_VERSION_CORE=8
G_DIETPI_VERSION_SUB=25
G_DIETPI_VERSION_RC=1
G_GITBRANCH=‘master’
G_GITOWNER=‘MichaIng’ -
Distro version
bookworm 0 -
Kernel version
Linux dietpi 6.1.21-v8+ #1642 SMP PREEMPT Mon Apr 3 17:24:16 BST 2023 aarch64 GNU/Linux -
Architecture
arm64 -
SBC model
RPi 4 Model B (aarch64) -
Software title
Unbound -
Was the software title installed freshly or updated/migrated?
Fresh from dietpi-software, pi-hole was already installed from dietpi-software too -
Can this issue be replicated on a fresh installation of DietPi?
Haven’t tried
I am trying to make Unbound work on my Pi-hole home setup but something is not working properly and i have no internet connection.
Unbound is successfully installed from dietpi-software and is properly adjusting the settings in Pi-hole.
Here some logs:
root@dietpi:~# systemctl status unbound
● unbound.service - Unbound DNS server
Loaded: loaded (/lib/systemd/system/unbound.service; enabled; preset: enabled)
Drop-In: /etc/systemd/system/unbound.service.d
└─dietpi.conf
Active: active (running) since Fri 2024-01-19 14:24:34 EET; 1min 3s ago
Docs: man:unbound(8)
Process: 420 ExecStartPre=/usr/libexec/unbound-helper chroot_setup (code=exited, status=0/SUCCESS)
Process: 480 ExecStartPre=/usr/libexec/unbound-helper root_trust_anchor_update (code=exited, status=0/SUCCESS)
Main PID: 482 (unbound)
Tasks: 1 (limit: 2197)
CPU: 355ms
CGroup: /system.slice/unbound.service
└─482 /usr/sbin/unbound -d -p
Jan 19 14:24:33 dietpi systemd[1]: Starting unbound.service - Unbound DNS server...
Jan 19 14:24:34 dietpi unbound[482]: [482:0] warning: subnetcache: serve-expired is set but not working for data originating from the subnet module cache.
Jan 19 14:24:34 dietpi unbound[482]: [482:0] warning: subnetcache: prefetch is set but not working for data originating from the subnet module cache.
Jan 19 14:24:34 dietpi unbound[482]: [482:0] info: start of service (unbound 1.17.1).
Jan 19 14:24:34 dietpi systemd[1]: Started unbound.service - Unbound DNS server.
root@dietpi:~# journalctl -u unbound
Jan 19 14:24:33 dietpi systemd[1]: Starting unbound.service - Unbound DNS server...
Jan 19 14:24:34 dietpi unbound[482]: [482:0] warning: subnetcache: serve-expired is set but not working for data originating from the subnet module cache.
Jan 19 14:24:34 dietpi unbound[482]: [482:0] warning: subnetcache: prefetch is set but not working for data originating from the subnet module cache.
Jan 19 14:24:34 dietpi unbound[482]: [482:0] info: start of service (unbound 1.17.1).
Jan 19 14:24:34 dietpi systemd[1]: Started unbound.service - Unbound DNS server.
root@dietpi:~# ss -tulpn | grep LISTEN
tcp LISTEN 0 5 127.0.0.1:4711 0.0.0.0:* users:(("pihole-FTL",pid=444,fd=10))
tcp LISTEN 0 1024 0.0.0.0:443 0.0.0.0:* users:(("lighttpd",pid=648,fd=5))
tcp LISTEN 0 511 127.0.0.1:6379 0.0.0.0:* users:(("redis-server",pid=412,fd=7))
tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:* users:(("mariadbd",pid=479,fd=20))
tcp LISTEN 0 256 127.0.0.1:5335 0.0.0.0:* users:(("unbound",pid=482,fd=4))
tcp LISTEN 0 1000 0.0.0.0:22 0.0.0.0:* users:(("dropbear",pid=400,fd=3))
tcp LISTEN 0 32 0.0.0.0:53 0.0.0.0:* users:(("pihole-FTL",pid=444,fd=5))
tcp LISTEN 0 1024 0.0.0.0:80 0.0.0.0:* users:(("lighttpd",pid=648,fd=7))
tcp LISTEN 0 1024 [::]:443 [::]:* users:(("lighttpd",pid=648,fd=6))
tcp LISTEN 0 1000 [::]:22 [::]:* users:(("dropbear",pid=400,fd=4))
tcp LISTEN 0 32 [::]:53 [::]:* users:(("pihole-FTL",pid=444,fd=7))
tcp LISTEN 0 1024 [::]:80 [::]:* users:(("lighttpd",pid=648,fd=4))
root@dietpi:~# dig @127.0.0.1 -p 5335 google.com
;; communications error to 127.0.0.1#5335: timed out
;; communications error to 127.0.0.1#5335: timed out
;; communications error to 127.0.0.1#5335: timed out
; <<>> DiG 9.18.19-1~deb12u1-Debian <<>> @127.0.0.1 -p 5335 google.com
; (1 server found)
;; global options: +cmd
;; no servers could be reached
root@dietpi:~# cat /etc/resolv.conf
nameserver 192.168.1.1
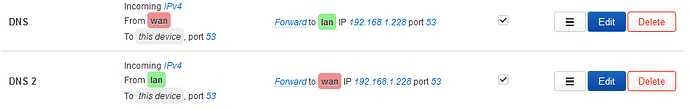
192.168.1.1 is the IP of my openwrt router which is running stubby for DOT and with DNS forwardings at 127.0.0.1#5453 with both “DNSSEC” and “DNSSEC check unsigned” enabled, this is what i was using for upstream DNS in Pi-hole before trying Unbound.
The router gives a static IP to my dietpi and that IP is used on my home devices for DNS Adblocking though Pi-hole. The DHCP server of Pi-hole is not running.
Any help appreciated, really want to test Unbound.