Hi Community,
I have a raspberry Pi which connects via WireGuard to a VServer and which is located behind my fritzbox router.
I want to route all traffic on my network through the VPN gateway but can‘t figure out how to set the static routing.
My IPs:
fritzbox: 192.168.178.1, 255.255.255.0
DHCP: 192.168.178.20-200
Raspberry: 192.168.178.52, does pihole as well (eth0)
WireGuard: 172.16.100.5 (wg0)
It should be possible to route all traffic coming to the fritzbox through 192.168.178.52, right?
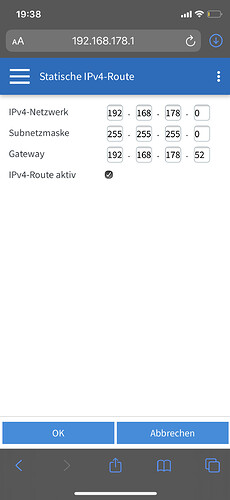
I was trying to set the routing as shown in the screenshot but that resulted in not beeing able to access my fritzbox anymore…
Does anybody have any advise what to set on my fritzbox?
Thanks in advance!
You mean you want all systems in your local network to use the VPN? I don’t know any way how to configure this in the router, especially on fritzbox, but of course you can setup a WireGuard client on all systems to connect with the DietPi WireGuard system, so they use it for all outgoing traffic.
Since connected clients do not listen/answer to incoming connections outside the VPN tunnel anymore, practically only connections coming through the tunnel are handled.
I guess all clients (not the F!B) needs to be configured that way, that the RPi is the Gateway and not the F!B. And of course you are not able to access your F!B anymore once you activated your route. Because the F!B will route entire traffic of 192.168.178.0 network to the RPi, even the traffic to access your F!B  Means, only local network IP addresses will be routed. Not the internet traffic.
Means, only local network IP addresses will be routed. Not the internet traffic.
But yeah, maybe you can let us know what your scenario is. Why do you need to route your entire traffic to the vServer?
I would forget about the gateway topic, as this wound only mess with the clean full VPN tunnel setup.
Simply install WireGuard on all systems (it is available for nearly all OS). Create client configs on the DietPi system according to our docs: https://dietpi.com/forum/t/dietpi-software-details-for-all-installation-options/22/127
Move and use the generated client configs and private keys on the clients. By default the configs include that WireGuard on the clients sets up routes so that all outgoing traffic is tunnelled and incoming traffic outside the VPN is ignored. That’s it.
But I understood it that way, that there is a just a WireGuard Client running on DietPi and the vServer is hosting the WireGuard Server. This way, you would need to create all the client configs on the vServer 
Would be great to know a little bit more about the setup and scenario
Ah okay, same procedure still, then on the vServer. Changing the gateway btw is generally the wrong attempt since then clients cannot connect to the server. The gateway stays as it is to have all clients connected to the same network. The routes created by WireGuard clients is what forces tunnelled traffic, once connected.
Thanks for your replies! My setup is as follows:
I have a Vserver which is running as my wireguard server.
To it my Raspberry connects as a client. I wanted to use the Raspberry as a gateway behind my fritzbox without having to need to configure every client on my network. I want all my traffic to flow through the Raspberry to my Server.
I got it working by enabling dhcp Server on my pihole installation 
and what is the Router Gateway you specified inside PiHole?
Okay now the idea gets clear. Sounds reasonable but AFAIK not an easy task.
- DietPi needs VPN connection, okay that is easy
- DietPi needs to be setup as NAT to share it’s network access and forward incoming requests. With WiFi as access point and Ethernet for router/internet this can be done via WiFi hotspot install on dietpi-software and dietpi-config. But the other way round or with two WiFi or two Ethernet this needs manual interface + iptables setup.
But now the difficult task is to not forward incoming traffic to the internet adapter interface but to the WireGuard client interface, e.g. wg0 or what it is called. Furthermore DietPi needs to forward answers back to the clients and I am not sure if the default WireGuard routes force all answers back through WireGuard (so clients are never answered) or if iptables forward rules override the routes. Needs testing. So first attempt would be to change the iptables rules and replace adapter instance with WireGuard interface. If this does not work, then the AllowedIPs setting in WireGuard config on DietPi needs to be adjusted to exclude (only) all IPs to local network. If this still does not work, further web search is required as I am out of ideas then for now  .
.
unfortunately I don’t have an external WireGuard Server that I could use for testing. Otherwise I would play around with it 
I specified 192.168.178.52 as Gateway…
Pls van you post ip -a as weil as ip -r from your RPi
Whether external or internal should not play a major role, hence testing with local VM should be possible add well. But I’ll not find some time soon  .
.