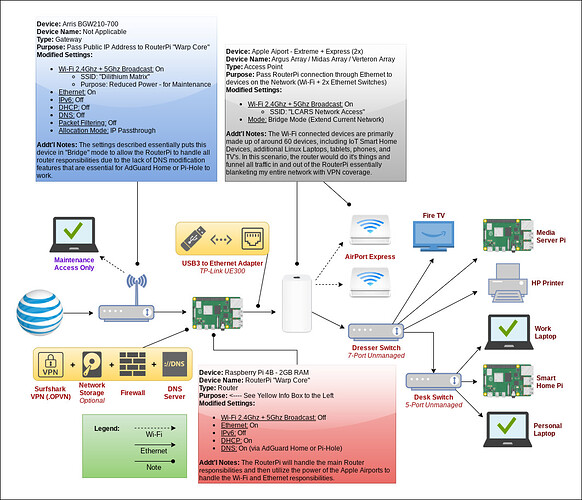
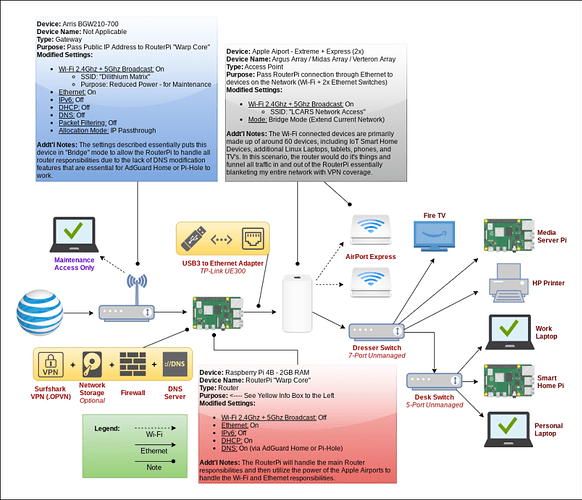
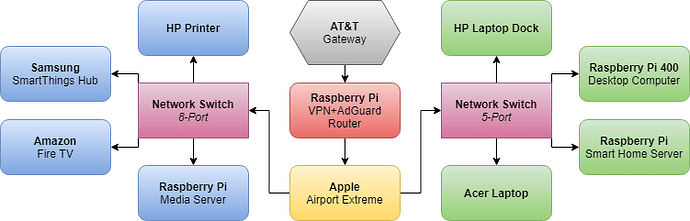
Greetings,
I know this topic has been discussed many time, and I assure you I have found and tested close to 100 tutorials, forum topics and posts, articles, and more on this topic - however, I have yet to find anything that has worked for my specific situation (specifically with my current ISP gateway/router being a PITA to customize). They either didn’t work due to my hardware limitations, their hardware limitations (specifically the use of a USB-to-Ethernet Adapter), or because I just didn’t understand what was being done in the background which would have allowed me to change metrics to fit my needs. With that said, I need some help: Below you will find more information regarding my specific situation, including what I have already attempted to use - I would greatly appreciate any instruction, feedback, and/or resources to assist me in setting up my network using the Pi in the way that I have illustrated in the attached diagram below (i.e.; using the Pi has a VPN Tunnel/Gateway + AdGuard Home Server + Firewall). Now, on to the specifics…
Due to the fact that I am using Surfshark VPN, a lot of the tutorials don’t offer the ability to customize the actual VPN provider. With that said, I will need to use the standard OpenVPN software so I can using Surfshark’s OPVN file and certificates.
Some might say, “Why don’t you just use your current ISP’s router/gateway to add your AdGuard Home’s DNS entries and Surfshark’s VPN configuration, or put the ISP’s router/gateway into bridge mode and use your Apple AirPort Extreme as the router?” Well that is a long winded response, but here is the short answer: I am using AT&T’s fiber connection that utilizes the Arris BGW210-700 gateway/router which has no options for bridge mode (which is why you will see all the modified settings in the image below that I had to incorporate to create a pseudo “bridge mode”), nor does it allow me to change the DNS. Additionally, the Apple AirPort devices are simply old, out-of-date (the Extreme has a USB port for network HDD/SSD connections but it uses SMB1 which is no longer secure and my Windows computers won’t connect to it), and are also more locked down than current router offerings. These reasons are why I’d like to use the Pi as as a router, and the AirPort devices as a bridged wireless and wired access point.
Below you will find some of the more common solutions that I have tested without full success:
-
OpenWRT: Includes ability to add VPN and Ad Block Apps once the software is setup on the Pi, but the only available firmware available for the Pi 4 is their “snapshot” (which makes updating a big mess) or their community builds (which also requires an extended and messy update process). Once they release their newest version (20 something), this option will be used unless someone here can provide me with a rock-solid method of setting up the Pi with my desired requirements.
-
RaspAP: Includes OpenVPN + Built-in Ad Blocking (both customizable), but no support for USB-to-Ethernet Adapters. This setup seemed to be one of the better options, but again, it was only intended to be a HotSpot or AP Bridge. I followed their instructions and also found another good tutorial about how to set it up with NordVPN instead of Surfshark, but the instructions seem to be missing some steps and its meant to be used as a Wi-Fi HotSpot.
-
Pantacore One: Includes Remote Access to Router via their website Hub + Wireguard and Tailscail VPN Apps + NextCloud App + Cloudfare Warp + Home Assistant App, but no support for USB-to-Ethernet Adapters (again, I don’t want to use the Pi as a HotSpot because the Pi’s Wi-Fi antenna is very weak and only broadcasts one band). I also didn’t like the fact that this system is somewhat “locked-down” and I am not able to see the coding of where my data is being sent.
-
Mr. Canoehead - VPN Client Gateway
-
Pi-Hole with PiVPN (They have tutorials for using OpenVPN or Wireguard as a Gateway/Tunnel rather than a Server) - It is hit-or-miss as to how well it’s documented - it also isn’t that easy to understand what they are saying since most of their documentation is community submitted.
-
ShVerni - Raspberry Pi VPN Gateway
- Custom Setup using DietPi’s HotSpot + OpenVPN (via Surfshark’s OPVN Config Files) + Modifying IP Tables and IP Forwarding - I attempted to incorporate multiple tutorials/guides that I’ve seen (along with some knowledge that I’ve gain from reading all of these guides) to incorporate my Surfshark VPN requirements, and use my USB-to-Ethernet adapter to pass the Pi’s router responsibilities to the Apple Airport Extreme.
-
Raspberry Pi Foundations Routed Access Point Guide
- Docker Containers / Virtual Machines: I have tried to play around with Docker and Portainer to see what it’s all about, but unfortunately I still do not know how it works or how to set one up - with that said, I did see some folks using OpenWRT, pFSense, OPNSense, etc. within a Virtual Container or Virtual Machine. Again, I understand the concept of routing traffic through the virtual network connections, but still do not understand how to do it (same goes for running a VPN Gateway/Tunnel through it).
- Many, many, many other Tutorials found through hours of Google Searching
So, now you might ask, “What exactly are your goals?” - see list below, and the attached network configuration image:
- VPN Gateway
- AdGuard Home Ad-Blocking
- Firewall (I know the Raspberry Pi’s have their own, but I was interested in what others are using and would recommend)
- File & Media Server (Optional because I currently have a dedicated Pi running a simple Samba and Jellyfin Server)
Now that you have seen how I would like this to work and what devices I would like to use (or at least an estimate based on my current knowledge of how these things should work), below are the available “extra” devices that I can use in additional to the above devices shown in the picture:
- TP-Link USB 3.0-to-Ethernet Adapter (UE300)
- TP-Link R370K + AC1200 (Extender + Smart Plug)
- TP-Link N300 (Travel Router)
- Raspberry Pi 4B - 2GB RAM (2x)
- Raspberry Pi 400
My only other option to incorporate the above listed requirements is to buy a cheap (relatively speaking) router that has multiple ethernet ports, at least one USB 3.0 port to setup my File and Media Server on, and allows me to flash the OpenWRT (or ASUS-WRT for ASUS Routers) firmware to it for VPN and Ad-Blocking functionality. I’d rather now spend the money ($100 or less) on a new or used router to accomplish this type of setup since it really seems these Pi’s are fully capable of handling the tasks I mentioned above.
Additional Questions:
- I used to be a web designer in my previous life, however I have decided to keep my reseller hosting account and my 100+ domain names. How can I better utilize my hosting server and domain names to access certain parts of my home network (such as my File and Media Server, Home Assistant, potentially an Ad Block Server to connect to when away from home, etc.)?
- Generally speaking, what is the best way to secure the setup I mentioned above, and all other Pi’s on my network? I have heard of Unbound, No-IP, Let’s Encrypt, DoH, QoS, etc. but since my knowledge of remote access networking is more limited that my knowledge of Linux/Raspberry Pi (which I would consider to be a little higher than beginner), I would rather hear from others as to what they prefer and how they are implementing it.
- I am looking to start a Pi project that uses a dedicated Pi within my network that is to be used as a centralized and remote web browser so that I can, for example, use Chrome or Firefox on multiple computers via a remote desktop app that have all of my current tabs open (rather than having to bookmark all open tabs and reopen when using a different computer). This may sound pointless to some, but I have many laptops (most are stationary and are docked) that I use around my home (inside and outside) and I am tired of having to save bookmarks or sync tabs to re-open when I stop working on one computer to go have a smoke outside (and use a different laptop on the patio). I’d rather simply open up a remote desktop app, connect to the Pi, and continue from where I left off. Since remote desktops have gotten better over the years, I figure this is a good option, but I would like to inquire as to what software people prefer. DietPi has multiple offerings, including NoMachine, remote.it, and others. I have also researched other options like ZeroTier. Thoughts?
Hopefully this all makes sense. I apologize for the length of the post, but I needed to ensure that I explained everything.
Any help is greatly appreciated!