hhmmmm Still no go… 
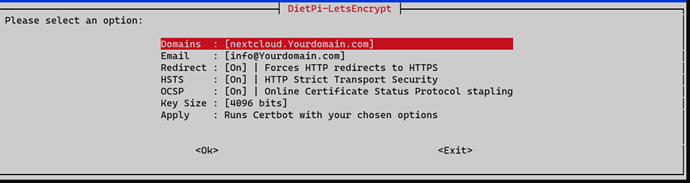
After installation of NC i ran Let’s Encrypt with the subdomain: nextcloud.Yourdomain.com
And options set to ON
.
With NC it is visible
But not via DNS !?
With https://Yourdomain.com/nextcloud/ I got
Your connection is not private
Cyber criminals may be trying to steal your information from hemertje.com (for example, passwords, messages, or credit card information). More information
NET::ERR_CERT_COMMON_NAME_INVALID
With https://nextcloud.Yourdomain.com/ I got
Welcome to nginx!
If you see this page, the nginx web server is successfully installed and working. Further configuration is required.
For online documentation and support please refer to nginx.org.
Commercial support is available at nginx.com.
Thank you for using nginx.
So I edited
nano /var/www/nextcloud/config/config.php
And adjust value overwrite.cli.url
Remove the sub path /nextcloud from
‘overwrite.cli.url’ => ‘https://nextcloud.Yourdomain.com/nextcloud’,
Should looks like this now
‘overwrite.cli.url’ => ‘https://nextcloud.Yourdomain.com’,
Save and Close nano with CNTR+O ans CNTRL+X.
restart the Nginx webserver
systemctl restart nginx
In the hope that with https://nextcloud.Yourdomain.com NC would be accesseble!
Now on Local IP I even can’t login anymore
I get rejected…
https:// < local IP> /nextcloud/login?redirect_url=/nextcloud/apps/dashboard/
My 2 config files:
nano /var/www/nextcloud/config/config.php
<?php
$CONFIG = array (
'passwordsalt' => 'hjQ4NMRn4UUU49svfnqrkfjnqwrkjn38772Jf',
'secret' => 'ASdk6FVSA6+RC34972398y123r9y +peIW1aRqajkEIx6ynqH',
'trusted_domains' =>
array (
0 => 'localhost',
1 => '*',
),
'datadirectory' => '/mnt/dietpi_userdata/nextcloud_data',
'dbtype' => 'mysql',
'version' => '25.0.2.3',
'hashingThreads' => 6,
'memcache.local' => '\\OC\\Memcache\\APCu',
'filelocking.enabled' => true,
'memcache.locking' => '\\OC\\Memcache\\Redis',
'redis' =>
array (
'host' => '/run/redis/redis-server.sock',
'port' => 0,
),
'overwrite.cli.url' => 'https://nextcloud.Yourdomain.com',
'dbname' => 'nextcloud',
'dbhost' => 'localhost',
'dbport' => '',
'dbtableprefix' => 'oc_',
'mysql.utf8mb4' => true,
'dbuser' => 'oc_admin',
'dbpassword' => '8sWa=)passwordb}9:Q,wtU$?k6&',
'installed' => true,
'instanceid' => 'octiwengfbzo9g5',
'mail_from_address' => '?',
'mail_smtpmode' => 'smtp',
'mail_sendmailmode' => 'smtp',
'mail_domain' => 'Yourdomain.com',
'mail_smtphost' => 'mail.mailserver.net',
'mail_smtpsecure' => 'ssl',
'mail_smtpport' => '465',
'mail_smtpauthtype' => 'LOGIN',
'mail_smtpauth' => 1,
'mail_smtpname' => 'info@Yourdomain.com',
'mail_smtppassword' => '@password.comt',
'default_phone_region' => 'optional',
);
nano /etc/nginx/sites-dietpi/dietpi-nextcloud.conf
# Based on: https://github.com/nextcloud/documentation/blob/master/admin_manual/installation/nginx-subdir.conf.sample
# Redirect webfinger and nodeinfo requests to Nextcloud endpoint
location /.well-known/webfinger { return 301 /nextcloud/index.php$request_uri; }
location /.well-known/nodeinfo { return 301 /nextcloud/index.php$request_uri; }
location ^~ /nextcloud {
# Omit Nginx version on error response
server_tokens off;
# Set max upload size
client_max_body_size 1048576M;
fastcgi_buffers 64 4K;
# Enable gzip but do not remove ETag headers
gzip on;
gzip_vary on;
gzip_comp_level 4;
gzip_min_length 256;
gzip_proxied expired no-cache no-store private no_last_modified no_etag auth;
gzip_types application/atom+xml application/javascript application/json application/ld+json application/manifes>
# HTTP response headers borrowed from Nextcloud `.htaccess`
add_header Strict-Transport-Security "max-age=15768000; includeSubDomains" always;
add_header Referrer-Policy "no-referrer" always;
add_header X-Content-Type-Options "nosniff" always;
add_header X-Download-Options "noopen" always;
add_header X-Frame-Options "SAMEORIGIN" always;
add_header X-Permitted-Cross-Domain-Policies "none" always;
add_header X-Robots-Tag "none" always;
add_header X-XSS-Protection "1; mode=block" always;
# Remove X-Powered-By, which is an information leak
fastcgi_hide_header X-Powered-By;
# Specify how to handle directories -- specifying `/nextcloud/index.php$request_uri`
# here as the fallback means that Nginx always exhibits the desired behaviour
# when a client requests a path that corresponds to a directory that exists
# on the server. In particular, if that directory contains an index.php file,
# that file is correctly served; if it doesn't, then the request is passed to
# the front-end controller. This consistent behaviour means that we don't need
# to specify custom rules for certain paths (e.g. images and other assets,
# `/updater`, `/ocm-provider`, `/ocs-provider`), and thus
# `try_files $uri $uri/ /nextcloud/index.php$request_uri`
# always provides the desired behaviour.
index index.php index.html /nextcloud/index.php$request_uri;
# Rule borrowed from `.htaccess` to handle Microsoft DAV clients
location = /nextcloud {
if ( $http_user_agent ~ ^DavClnt ) {
return 302 /nextcloud/remote.php/webdav/$is_args$args;
}
}
# Rules borrowed from `.htaccess` to hide certain paths from clients
location ~ ^/nextcloud/(?:build|tests|config|lib|3rdparty|templates|data)(?:$|/) { return 404; }
location ~ ^/nextcloud/(?:\.|autotest|occ|issue|indie|db_|console) { return 404; }
# Ensure this block, which passes PHP files to the PHP process, is above the blocks
# which handle static assets (as seen below). If this block is not declared first,
# then Nginx will encounter an infinite rewriting loop when it prepends
# `/nextcloud/index.php` to the URI, resulting in a HTTP 500 error response.
location ~ \.php(?:$|/) {
fastcgi_split_path_info ^(.+?\.php)(/.*|)$;
set $path_info $fastcgi_path_info;
try_files $fastcgi_script_name =404;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_param HTTPS $https;
fastcgi_param modHeadersAvailable true; # Avoid sending the security headers twice
fastcgi_param front_controller_active true; # Enable pretty URLs without /index.php/
fastcgi_pass php;
fastcgi_intercept_errors on;
fastcgi_request_buffering off;
fastcgi_max_temp_file_size 0; # Allow downloads > 1 GiB: https://github.com/nextcloud/documentation/pul>
}
location ~ \.(?:css|js|svg|gif|png|jpg|ico|wasm|tflite|map)$ {
try_files $uri /nextcloud/index.php$request_uri;
expires 6M; # Cache-Control policy borrowed from `.htaccess`
access_log off; # Optional: Don't log access to assets
}
location ~ \.woff2?$ {
try_files $uri /nextcloud/index.php$request_uri;
expires 7d; # Cache-Control policy borrowed from `.htaccess`
access_log off; # Optional: Don't log access to assets
}
# Rule borrowed from `.htaccess`
location /nextcloud/remote {
return 301 /nextcloud/remote.php$request_uri;
}
location /nextcloud {
try_files $uri $uri/ /nextcloud/index.php$request_uri;
}
}
Help, what goes wrong?