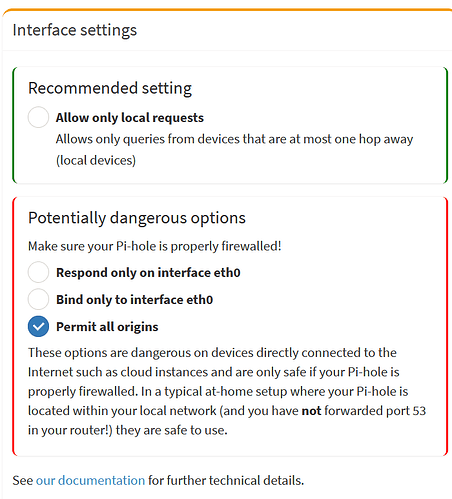
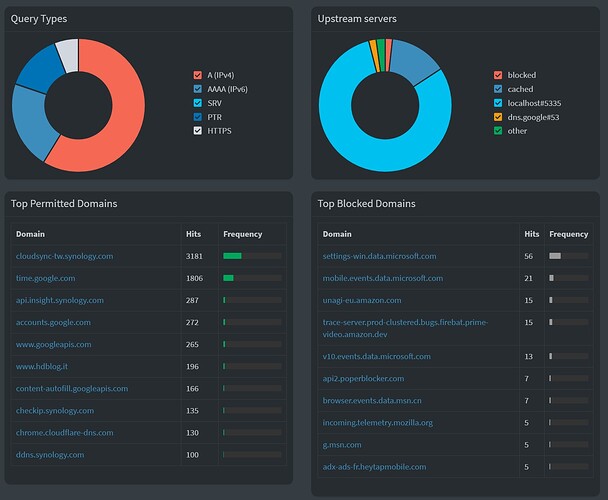
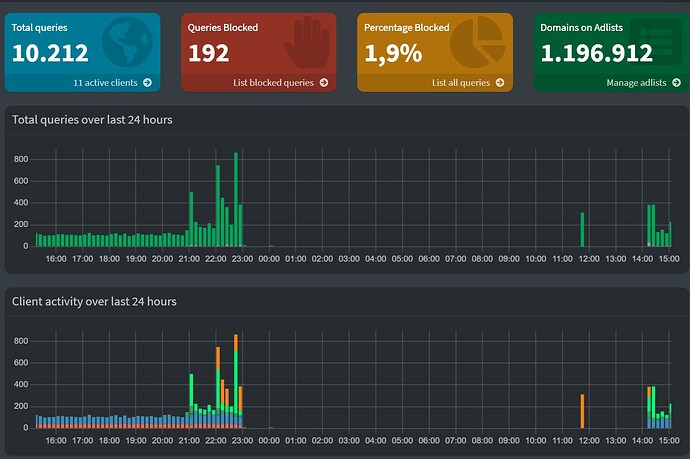
I did a pihole reset later last night, maybe some data has been lost, but it always worked fine.
tcpdump
15:40:37.457656 IP f.root-servers.net.domain > 192.168.1.87.51810: 37884 ServFail* 0/0/1 (28)
15:40:37.458048 IP 192.168.1.87.19783 > M.ROOT-SERVERS.NET.domain: 31817% [1au] NS? . (28)
15:40:37.459228 IP M.ROOT-SERVERS.NET.domain > 192.168.1.87.19783: 31817 ServFail* 0/0/1 (28)
15:40:37.459636 IP 192.168.1.87.30129 > j.root-servers.net.domain: 34155% [1au] NS? . (28)
15:40:37.461058 IP j.root-servers.net.domain > 192.168.1.87.30129: 34155 ServFail* 0/0/1 (28)
15:40:37.461434 IP 192.168.1.87.61137 > M.ROOT-SERVERS.NET.domain: 41328% [1au] NS? . (28)
15:40:37.462499 IP M.ROOT-SERVERS.NET.domain > 192.168.1.87.61137: 41328 ServFail* 0/0/1 (28)
15:40:37.462931 IP 192.168.1.87.19447 > f.root-servers.net.domain: 37854% [1au] NS? . (28)
15:40:37.464073 IP f.root-servers.net.domain > 192.168.1.87.19447: 37854 ServFail* 0/0/1 (28)
15:40:37.464454 IP 192.168.1.87.51328 > a.root-servers.net.domain: 60186% [1au] NS? . (28)
15:40:37.465522 IP a.root-servers.net.domain > 192.168.1.87.51328: 60186 ServFail* 0/0/1 (28)
15:40:37.465900 IP 192.168.1.87.33286 > a.root-servers.net.domain: 10273% [1au] NS? . (28)
15:40:37.466956 IP a.root-servers.net.domain > 192.168.1.87.33286: 10273 ServFail* 0/0/1 (28)
15:40:37.467338 IP 192.168.1.87.21447 > M.ROOT-SERVERS.NET.domain: 57837% [1au] NS? . (28)
15:40:37.468529 IP M.ROOT-SERVERS.NET.domain > 192.168.1.87.21447: 57837 ServFail* 0/0/1 (28)
15:40:37.468922 IP 192.168.1.87.45657 > j.root-servers.net.domain: 26772% [1au] NS? . (28)
15:40:37.470102 IP j.root-servers.net.domain > 192.168.1.87.45657: 26772 ServFail* 0/0/1 (28)
15:40:37.470483 IP 192.168.1.87.44604 > e.root-servers.net.domain: 56810% [1au] NS? . (28)
15:40:37.471544 IP e.root-servers.net.domain > 192.168.1.87.44604: 56810 ServFail* 0/0/1 (28)
15:40:37.471928 IP 192.168.1.87.38035 > l.root-servers.net.domain: 10400% [1au] NS? . (28)
15:40:37.472822 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1558486, win 252, length 0
15:40:37.472907 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1558486:1558712, ack 7, win 501, length 226
15:40:37.472987 IP l.root-servers.net.domain > 192.168.1.87.38035: 10400 ServFail* 0/0/1 (28)
15:40:37.473371 IP 192.168.1.87.45137 > i.root-servers.net.domain: 5368% [1au] NS? . (28)
15:40:37.474427 IP i.root-servers.net.domain > 192.168.1.87.45137: 5368 ServFail* 0/0/1 (28)
15:40:37.474884 IP 192.168.1.87.48526 > G.ROOT-SERVERS.NET.domain: 57460% [1au] NS? . (28)
15:40:37.476134 IP G.ROOT-SERVERS.NET.domain > 192.168.1.87.48526: 57460 ServFail* 0/0/1 (28)
15:40:37.476547 IP 192.168.1.87.10864 > M.ROOT-SERVERS.NET.domain: 56016% [1au] NS? . (28)
15:40:37.477573 IP M.ROOT-SERVERS.NET.domain > 192.168.1.87.10864: 56016 ServFail* 0/0/1 (28)
15:40:37.477955 IP 192.168.1.87.58638 > l.root-servers.net.domain: 59897% [1au] NS? . (28)
15:40:37.479146 IP l.root-servers.net.domain > 192.168.1.87.58638: 59897 ServFail* 0/0/1 (28)
15:40:37.479531 IP 192.168.1.87.50395 > h.root-servers.net.domain: 959% [1au] NS? . (28)
15:40:37.481120 IP h.root-servers.net.domain > 192.168.1.87.50395: 959 ServFail* 0/0/1 (28)
15:40:37.481501 IP 192.168.1.87.32943 > i.root-servers.net.domain: 28463% [1au] NS? . (28)
15:40:37.482554 IP i.root-servers.net.domain > 192.168.1.87.32943: 28463 ServFail* 0/0/1 (28)
15:40:37.483003 IP 192.168.1.87.56750 > k.root-servers.net.domain: 18106% [1au] NS? . (28)
15:40:37.484133 IP k.root-servers.net.domain > 192.168.1.87.56750: 18106 ServFail* 0/0/1 (28)
15:40:37.484510 IP 192.168.1.87.17947 > G.ROOT-SERVERS.NET.domain: 10571% [1au] NS? . (28)
15:40:37.485569 IP G.ROOT-SERVERS.NET.domain > 192.168.1.87.17947: 10571 ServFail* 0/0/1 (28)
15:40:37.485947 IP 192.168.1.87.27077 > i.root-servers.net.domain: 64938% [1au] NS? . (28)
15:40:37.487010 IP i.root-servers.net.domain > 192.168.1.87.27077: 64938 ServFail* 0/0/1 (28)
15:40:37.487384 IP 192.168.1.87.43477 > l.root-servers.net.domain: 23395% [1au] NS? . (28)
15:40:37.488583 IP l.root-servers.net.domain > 192.168.1.87.43477: 23395 ServFail* 0/0/1 (28)
15:40:37.488958 IP 192.168.1.87.28938 > b.root-servers.net.domain: 19178% [1au] NS? . (28)
15:40:37.490156 IP b.root-servers.net.domain > 192.168.1.87.28938: 19178 ServFail* 0/0/1 (28)
15:40:37.490528 IP 192.168.1.87.63341 > l.root-servers.net.domain: 36512% [1au] NS? . (28)
15:40:37.491598 IP l.root-servers.net.domain > 192.168.1.87.63341: 36512 ServFail* 0/0/1 (28)
15:40:37.491984 IP 192.168.1.87.44745 > h.root-servers.net.domain: 27254% [1au] NS? . (28)
15:40:37.493040 IP h.root-servers.net.domain > 192.168.1.87.44745: 27254 ServFail* 0/0/1 (28)
15:40:37.493413 IP 192.168.1.87.64559 > e.root-servers.net.domain: 64959% [1au] NS? . (28)
15:40:37.494482 IP e.root-servers.net.domain > 192.168.1.87.64559: 64959 ServFail* 0/0/1 (28)
15:40:37.494902 IP 192.168.1.87.64758 > j.root-servers.net.domain: 50188% [1au] NS? . (28)
15:40:37.496055 IP j.root-servers.net.domain > 192.168.1.87.64758: 50188 ServFail* 0/0/1 (28)
15:40:37.497402 IP 192.168.1.87.12944 > l.root-servers.net.domain: 5342% [1au] NS? . (28)
15:40:37.498677 IP l.root-servers.net.domain > 192.168.1.87.12944: 5342 ServFail* 0/0/1 (28)
15:40:37.499086 IP 192.168.1.87.50333 > e.root-servers.net.domain: 44189% [1au] NS? . (28)
15:40:37.500249 IP e.root-servers.net.domain > 192.168.1.87.50333: 44189 ServFail* 0/0/1 (28)
15:40:37.500630 IP 192.168.1.87.53130 > l.root-servers.net.domain: 8007% [1au] NS? . (28)
15:40:37.501691 IP l.root-servers.net.domain > 192.168.1.87.53130: 8007 ServFail* 0/0/1 (28)
15:40:37.502068 IP 192.168.1.87.20084 > f.root-servers.net.domain: 993% [1au] NS? . (28)
15:40:37.503133 IP f.root-servers.net.domain > 192.168.1.87.20084: 993 ServFail* 0/0/1 (28)
15:40:37.503521 IP 192.168.1.87.11857 > c.root-servers.net.domain: 30131% [1au] NS? . (28)
15:40:37.504587 IP c.root-servers.net.domain > 192.168.1.87.11857: 30131 ServFail* 0/0/1 (28)
15:40:37.504964 IP 192.168.1.87.65018 > h.root-servers.net.domain: 58488% [1au] NS? . (28)
15:40:37.506016 IP h.root-servers.net.domain > 192.168.1.87.65018: 58488 ServFail* 0/0/1 (28)
15:40:37.506392 IP 192.168.1.87.33559 > e.root-servers.net.domain: 35111% [1au] NS? . (28)
15:40:37.507459 IP e.root-servers.net.domain > 192.168.1.87.33559: 35111 ServFail* 0/0/1 (28)
15:40:37.507842 IP 192.168.1.87.61757 > h.root-servers.net.domain: 49557% [1au] NS? . (28)
15:40:37.508900 IP h.root-servers.net.domain > 192.168.1.87.61757: 49557 ServFail* 0/0/1 (28)
15:40:37.509283 IP 192.168.1.87.52948 > l.root-servers.net.domain: 13110% [1au] NS? . (28)
15:40:37.510997 IP l.root-servers.net.domain > 192.168.1.87.52948: 13110 ServFail* 0/0/1 (28)
15:40:37.511388 IP 192.168.1.87.42870 > G.ROOT-SERVERS.NET.domain: 11940% [1au] NS? . (28)
15:40:37.512570 IP G.ROOT-SERVERS.NET.domain > 192.168.1.87.42870: 11940 ServFail* 0/0/1 (28)
15:40:37.512943 IP 192.168.1.87.36683 > a.root-servers.net.domain: 62003% [1au] NS? . (28)
15:40:37.514012 IP a.root-servers.net.domain > 192.168.1.87.36683: 62003 ServFail* 0/0/1 (28)
15:40:37.514397 IP 192.168.1.87.36146 > k.root-servers.net.domain: 32255% [1au] NS? . (28)
15:40:37.515453 IP k.root-servers.net.domain > 192.168.1.87.36146: 32255 ServFail* 0/0/1 (28)
15:40:37.515835 IP 192.168.1.87.21562 > i.root-servers.net.domain: 7917% [1au] NS? . (28)
15:40:37.516895 IP i.root-servers.net.domain > 192.168.1.87.21562: 7917 ServFail* 0/0/1 (28)
15:40:37.517292 IP 192.168.1.87.21043 > b.root-servers.net.domain: 41413% [1au] NS? . (28)
15:40:37.518468 IP b.root-servers.net.domain > 192.168.1.87.21043: 41413 ServFail* 0/0/1 (28)
15:40:37.518885 IP 192.168.1.87.14708 > l.root-servers.net.domain: 11899% [1au] NS? . (28)
15:40:37.520566 IP l.root-servers.net.domain > 192.168.1.87.14708: 11899 ServFail* 0/0/1 (28)
15:40:37.520940 IP 192.168.1.87.15162 > h.root-servers.net.domain: 5% [1au] NS? . (28)
15:40:37.522139 IP h.root-servers.net.domain > 192.168.1.87.15162: 5 ServFail* 0/0/1 (28)
15:40:37.522543 IP 192.168.1.87.56980 > c.root-servers.net.domain: 53052% [1au] NS? . (28)
15:40:37.523581 IP c.root-servers.net.domain > 192.168.1.87.56980: 53052 ServFail* 0/0/1 (28)
15:40:37.523965 IP 192.168.1.87.57932 > k.root-servers.net.domain: 40971% [1au] NS? . (28)
15:40:37.525159 IP k.root-servers.net.domain > 192.168.1.87.57932: 40971 ServFail* 0/0/1 (28)
15:40:37.525545 IP 192.168.1.87.44868 > f.root-servers.net.domain: 28681% [1au] NS? . (28)
15:40:37.526607 IP f.root-servers.net.domain > 192.168.1.87.44868: 28681 ServFail* 0/0/1 (28)
15:40:37.526983 IP 192.168.1.87.53293 > M.ROOT-SERVERS.NET.domain: 65132% [1au] NS? . (28)
15:40:37.527382 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1558712, win 252, length 0
15:40:37.528203 IP M.ROOT-SERVERS.NET.domain > 192.168.1.87.53293: 65132 ServFail* 0/0/1 (28)
15:40:37.528580 IP 192.168.1.87.29468 > G.ROOT-SERVERS.NET.domain: 61230% [1au] NS? . (28)
15:40:37.529643 IP G.ROOT-SERVERS.NET.domain > 192.168.1.87.29468: 61230 ServFail* 0/0/1 (28)
15:40:37.530023 IP 192.168.1.87.15509 > M.ROOT-SERVERS.NET.domain: 7758% [1au] NS? . (28)
15:40:37.531182 IP M.ROOT-SERVERS.NET.domain > 192.168.1.87.15509: 7758 ServFail* 0/0/1 (28)
15:40:37.531566 IP 192.168.1.87.47601 > b.root-servers.net.domain: 50248% [1au] NS? . (28)
15:40:37.532624 IP b.root-servers.net.domain > 192.168.1.87.47601: 50248 ServFail* 0/0/1 (28)
15:40:37.533008 IP 192.168.1.87.49077 > k.root-servers.net.domain: 3927% [1au] NS? . (28)
15:40:37.534197 IP k.root-servers.net.domain > 192.168.1.87.49077: 3927 ServFail* 0/0/1 (28)
15:40:37.534578 IP 192.168.1.87.31674 > k.root-servers.net.domain: 57322% [1au] NS? . (28)
15:40:37.535642 IP k.root-servers.net.domain > 192.168.1.87.31674: 57322 ServFail* 0/0/1 (28)
15:40:37.536031 IP 192.168.1.87.45137 > l.root-servers.net.domain: 38300% [1au] NS? . (28)
15:40:37.538916 IP l.root-servers.net.domain > 192.168.1.87.45137: 38300 ServFail* 0/0/1 (28)
15:40:37.539299 IP 192.168.1.87.27366 > M.ROOT-SERVERS.NET.domain: 15894% [1au] NS? . (28)
15:40:37.540751 IP M.ROOT-SERVERS.NET.domain > 192.168.1.87.27366: 15894 ServFail* 0/0/1 (28)
15:40:37.541129 IP 192.168.1.87.58002 > d.root-servers.net.domain: 6515% [1au] NS? . (28)
15:40:37.542455 IP d.root-servers.net.domain > 192.168.1.87.58002: 6515 ServFail* 0/0/1 (28)
15:40:37.542886 IP 192.168.1.87.56082 > a.root-servers.net.domain: 4468% [1au] NS? . (28)
15:40:37.544159 IP a.root-servers.net.domain > 192.168.1.87.56082: 4468 ServFail* 0/0/1 (28)
15:40:37.544539 IP 192.168.1.87.52760 > k.root-servers.net.domain: 65022% [1au] NS? . (28)
15:40:37.545738 IP k.root-servers.net.domain > 192.168.1.87.52760: 65022 ServFail* 0/0/1 (28)
15:40:37.546110 IP 192.168.1.87.30118 > j.root-servers.net.domain: 26774% [1au] NS? . (28)
15:40:37.547436 IP j.root-servers.net.domain > 192.168.1.87.30118: 26774 ServFail* 0/0/1 (28)
15:40:37.547814 IP 192.168.1.87.38670 > d.root-servers.net.domain: 19630% [1au] NS? . (28)
15:40:37.549009 IP d.root-servers.net.domain > 192.168.1.87.38670: 19630 ServFail* 0/0/1 (28)
15:40:37.549386 IP 192.168.1.87.36974 > d.root-servers.net.domain: 35200% [1au] NS? . (28)
15:40:37.551893 IP d.root-servers.net.domain > 192.168.1.87.36974: 35200 ServFail* 0/0/1 (28)
15:40:37.552343 IP 192.168.1.87.domain > 91.81.136.146.47400: 17852 ServFail 0/0/0 (90)
15:40:37.647576 IP MR80X.domain > 192.168.1.87.53710: 37088 NXDomain 0/1/0 (166)
15:40:37.648144 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1558712:1558855, ack 7, win 501, length 143
15:40:37.649960 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [.], seq 1558855:1560315, ack 7, win 501, length 1460
15:40:37.651999 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [.], seq 1560315:1561775, ack 7, win 501, length 1460
15:40:37.652176 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1560315, win 255, length 0
15:40:37.652261 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1561775:1561955, ack 7, win 501, length 180
15:40:37.653774 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1561955, win 255, length 0
15:40:37.653829 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1561955:1563226, ack 7, win 501, length 1271
15:40:37.655642 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [.], seq 1563226:1564686, ack 7, win 501, length 1460
15:40:37.657482 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [.], seq 1564686:1566146, ack 7, win 501, length 1460
15:40:37.657625 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1564686, win 255, length 0
15:40:37.657681 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1566146:1566182, ack 7, win 501, length 36
15:40:37.659183 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1566182, win 255, length 0
15:40:37.659243 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1566182:1567320, ack 7, win 501, length 1138
15:40:37.661002 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [.], seq 1567320:1568780, ack 7, win 501, length 1460
15:40:37.662863 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [.], seq 1568780:1570240, ack 7, win 501, length 1460
15:40:37.663219 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1568780, win 255, length 0
15:40:37.663279 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1570240:1570537, ack 7, win 501, length 297
15:40:37.664222 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [.], seq 1570537:1571997, ack 7, win 501, length 1460
15:40:37.664423 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1570537, win 255, length 0
15:40:37.664476 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1571997:1572262, ack 7, win 501, length 265
15:40:37.666094 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1572262, win 255, length 0
15:40:37.730931 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1572262:1572346, ack 7, win 501, length 84
15:40:37.732004 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [.], seq 1572346:1573806, ack 7, win 501, length 1460
15:40:37.733795 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1573806, win 255, length 0
15:40:37.733848 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1573806:1574779, ack 7, win 501, length 973
15:40:37.748664 IP 192.168.1.87.5252 > 192.168.1.85.57923: Flags [P.], seq 33774:34065, ack 1, win 501, length 291
15:40:37.775261 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1574779, win 252, length 0
15:40:37.806215 IP 192.168.1.85.57923 > 192.168.1.87.5252: Flags [.], ack 34065, win 253, length 0
15:40:37.835044 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1574779:1574900, ack 7, win 501, length 121
15:40:37.885224 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1574900, win 251, length 0
15:40:37.885279 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1574900:1575572, ack 7, win 501, length 672
15:40:37.940369 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1575572, win 255, length 0
15:40:37.940420 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1575572:1575920, ack 7, win 501, length 348
15:40:37.994175 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1575920, win 254, length 0
15:40:38.042920 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1575920:1576024, ack 7, win 501, length 104
15:40:38.096839 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1576024, win 254, length 0
15:40:38.096894 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1576024:1576250, ack 7, win 501, length 226
15:40:38.151897 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1576250, win 253, length 0
15:40:38.151965 IP 192.168.1.87.5252 > 192.168.1.85.57926: Flags [P.], seq 1576250:1576598, ack 7, win 501, length 348
15:40:38.206057 IP 192.168.1.85.57926 > 192.168.1.87.5252: Flags [.], ack 1576598, win 251, length 0