I have a DietPi server on Raspberry Pi 4B on which I am running a Pi-hole and bunch of other stuff and everything worked fine so far. The local IPv4 address of my DietPi server is 192.168.50.234.
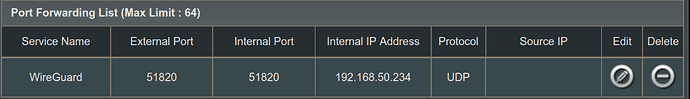
I have installed WireGuard using dietpi-software tool, which I configured as a server listening at the port 51820. I have enabled NAT port forwarding on my Asus RT-AX58U router as follows:
Then I generated a QR code from the preinstalled client config:
grep -v '^#' /etc/wireguard/wg0-client.conf | qrencode -t ansiutf8
and scanned that QR code with the WireGuard Android app. If I activate the VPN connection on my phone, I can’t access neither the local network nor the internet.
Here is the content of the configuration files:
dietpi@PiServer:~$ sudo cat /etc/wireguard/wg0.conf
[Interface]
Address = 10.9.0.1/24
PrivateKey = ***
ListenPort = 51820
PostUp = sysctl net.ipv4.conf.%i.forwarding=1 net.ipv4.conf.$(ip r l 0/0 | mawk '{print $5;exit}').forwarding=1
PostUp = sysctl net.ipv6.conf.$(ip r l 0/0 | mawk '{print $5;exit}').accept_ra=2
PostUp = sysctl net.ipv6.conf.%i.forwarding=1 net.ipv6.conf.$(ip r l 0/0 | mawk '{print $5;exit}').forwarding=1
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -s 10.9.0.0/24 -o $(ip r l 0/0 | mawk '{print $5;exit}') -j MASQUERADE
PostUp = ip6tables -A FORWARD -i %i -j ACCEPT; ip6tables -t nat -A POSTROUTING -o $(ip r l 0/0 | mawk '{print $5;exit}') -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -s 10.9.0.0/24 -o $(ip r l 0/0 | mawk '{print $5;exit}') -j MASQUERADE
PostDown = ip6tables -D FORWARD -i %i -j ACCEPT; ip6tables -t nat -D POSTROUTING -o $(ip r l 0/0 | mawk '{print $5;exit}') -j MASQUERADE
# Client 1
[Peer]
PublicKey = ***
AllowedIPs = 10.9.0.2/32
# Client 2
#[Peer]
#PublicKey = XXXX
#AllowedIPs = 10.9.0.3/32
dietpi@PiServer:~$ sudo cat /etc/wireguard/wg0-client.conf
[Interface]
Address = 10.9.0.2/24
PrivateKey = ***
# Comment the following to preserve the clients default DNS server, or force a desired one.
DNS = 192.168.50.234
# Kill switch: Uncomment the following, if the client should stop any network traffic, when disconnected from the VPN server
# NB: This requires "iptables" to be installed, thus will not work on most mobile phones.
#PostUp = iptables -I OUTPUT ! -o %i -m mark ! --mark $(wg show %i fwmark) -m addrtype ! --dst-type LOCAL -j REJECT; ip6tables -I OUTPUT ! -o %i -m mark ! --mark $(wg show %i fwmark) -m addrtype ! --dst-type LOCAL -j REJECT
#PreDown = iptables -D OUTPUT ! -o %i -m mark ! --mark $(wg show %i fwmark) -m addrtype ! --dst-type LOCAL -j REJECT; ip6tables -D OUTPUT ! -o %i -m mark ! --mark $(wg show %i fwmark) -m addrtype ! --dst-type LOCAL -j REJECT
[Peer]
PublicKey = ***
# Tunnel all network traffic through the VPN:
# AllowedIPs = 0.0.0.0/0, ::/0
# Tunnel access to server-side local network only:
# AllowedIPs = 192.168.50.0/24
# Tunnel access to VPN server only:
# AllowedIPs = 192.168.50.234/32
AllowedIPs = 0.0.0.0/0, ::/0
Endpoint = <MyPublicIPv4Address>:51820
# Uncomment the following, if you're behind a NAT and want the connection to be kept alive.
#PersistentKeepalive = 25
I believe this output is not OK (should contain more info):
dietpi@PiServer:~$ sudo wg
interface: wg0
public key: ***
private key: (hidden)
listening port: 51820
peer: ***
allowed ips: 10.9.0.2/32
However when I connected my phone to the WiFi in the same local network, I have successfully run
~ $ nc -zvu 192.168.50.234 51820
Connection to 192.168.50.234 51820 port [udp/*] succeeded!
which possibly means that the port is open at least from the local network.
What am I doing wrong, why can’t I connect?