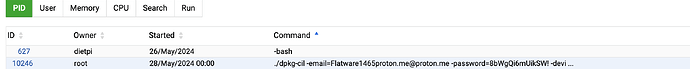
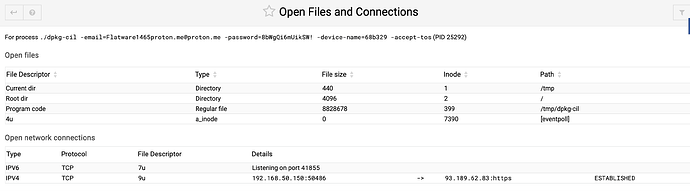
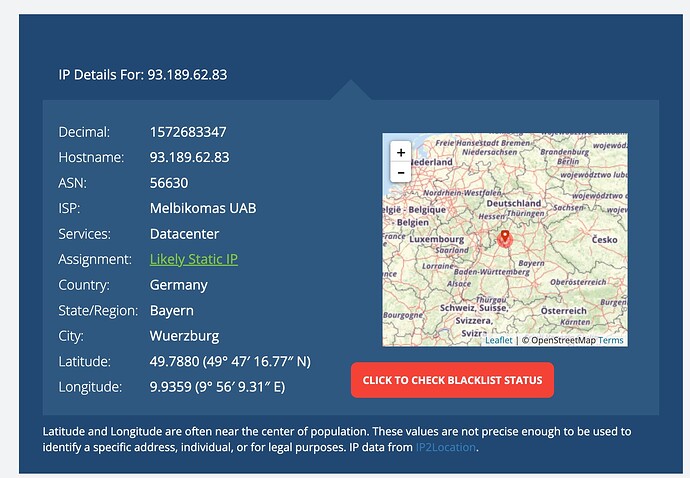
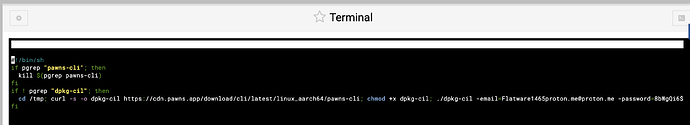
Just wondering what this process is and why its listed as an email with password. I killed the process last night but it is up again now.
You can try to get the whole process command to get better understanding on what exactly the process is trying to do
ps -ef | grep 10246
Assuming process id is still same
That gave me the same answer as webmin description:
root@DietPi:~# ps -ef | grep 25292
root 9698 8213 0 08:57 pts/0 00:00:00 grep 25292
root 25292 1 0 May28 ? 00:00:11 ./dpkg-cil -email=Flatware1465proton.me@proton.me -password=8bWgQi6mUikSW! -device-name=68b329 -accept-tos
Is there a way I can delete the process and files for good?
I checked the outgoing IP address and it is the same data center in Germany where I had a brute force attack weeks ago. Safe to say someone got in.
the main problem might be to find the trigger for this process. Actually it looks it is executed from /tmp. However this is just a tmpfs and will be deleted on reboot. I guess some other process or service will copy these files over into /tmp. Therefore deleting files will not do that much difference. You could try to search the executable. Maybe you will find it somewhere else?? Or you have a look into system log around the start time of the process.
I guess I will have to do some more investigation. For now I blocked the IP on my router and the DietPi is constantly on anyways. Since the process restarted without a reboot last time I guess some other live process is responsible for restarting it at midnight…
you could try to check all services available
systemctl list-units --all
it will be a long list ![]()
Solved…?
The process always started at 00:00 so I though to check the cron jobs and in the bottom I found two jobs both edited to start a program to listen in and open traffic to servers in Germany and the Netherlands.
The dpkg-compat included this line:
Now just to test it out I let the process run but deleted the file within the tmp folder which screws up the open tunnel (previously it listed my own ip plus whichever place it connected)
Can I then just delete the addition of this from the cron job?
Deleting that file should do it.
ps -fax will show the parent and the kiddos.
Hopefully it will show you who/what is executing this.
This topic was automatically closed 180 days after the last reply. New replies are no longer allowed.