its doesnt matter for me for best choico what you believe you can give me a suggestion
If you are not able to open ports on your router, you can use Tailscale
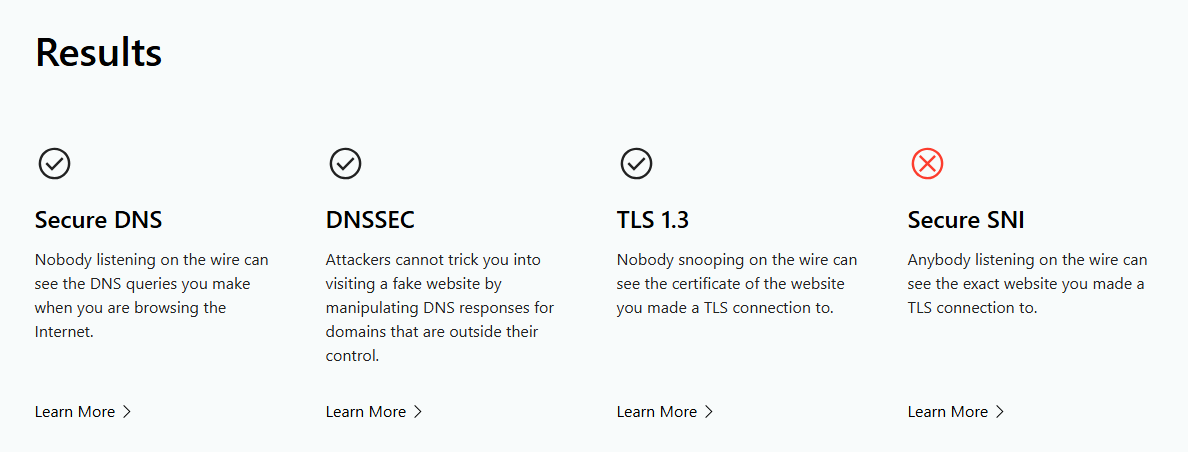
When i check Cloudflare Browser Check
Secure sni have error. thats happening beause Adguard dns upstream 192.168.1.1 ?
Secure SNI is a browser feature which has nothing to do with DNS. When I checked last, only Firefox did support it, not Chrome or any other Chromium-based browser.
Btw, that “Secure DNS” has a tick means, that this browser is not using your AdGuard/Unbound but DoH (DNS-over-HTTPS). You need to disable DoH in all browser, else they are bypassing your AdGuard Home or any other local DNS resolver.
When i change /etc/resolv.conf 127.0.0.1 instead of 192.168.1.1 then secu sni again active .
but then when i go adguard it say dns cant found by aduard. but adguard still works
dot not working after dietpi updated 9.8.0 to 9.9.0. it was working very good.
/etc/unbound/unbound.conf.d/dietpi.conf
Another question. Can i install 9.8.0 version without update first installion ?
i dont want update first installion
server:
# The verbosity number, level 0 means no verbosity, only errors.
# Level 1 gives operational information. Level 2 gives detailed
# operational information. Level 3 gives query level information,
# output per query. Level 4 gives algorithm level information.
# Level 5 logs client identification for cache misses. Default is
# level 1.
verbosity: 0
interface: 127.0.0.1
port: 53
do-ip4: yes
do-udp: yes
do-tcp: yes
# Unbound local queries needs to be off if using stubby or dnscrypt
do-not-query-localhost: no
# May be set to yes if you have IPv6 connectivity
do-ip6: yes
# You want to leave this to no unless you have *native* IPv6. With 6to4 and
# Terredo tunnels your web browser should favor IPv4 for the same reasons
prefer-ip6: no
# Use this only when you downloaded the list of primary root servers!
# Read the root hints from this file. Make sure to
# update root.hints evry 5-6 months.
root-hints: "/var/lib/unbound/root.hints"
# Trust glue only if it is within the servers authority
harden-glue: yes
# Ignore very large queries.
harden-large-queries: yes
# Require DNSSEC data for trust-anchored zones, if such data is absent, the zone becomes BOGUS
# If you want to disable DNSSEC, set harden-dnssec stripped: no
harden-dnssec-stripped: yes
# Enable DNSSEC with auto-trust-anchor root.key
#auto-trust-anchor-file: "/var/lib/unbound/root.key"
# Can be uncommented if you do not need file access protection
#chroot: ""
# Number of bytes size to advertise as the EDNS reassembly buffer
# size. This is the value put into datagrams over UDP towards
# peers. The actual buffer size is determined by msg-buffer-size
# (both for TCP and UDP).
edns-buffer-size: 1232
# Rotates RRSet order in response (the pseudo-random
# number is taken from Ensure privacy of local IP
# ranges the query ID, for speed and thread safety).
# private-address: 192.168.0.0/16
rrset-roundrobin: yes
# Time to live minimum for RRsets and messages in the cache. If the minimum
# kicks in, the data is cached for longer than the domain owner intended,
# and thus less queries are made to look up the data. Zero makes sure the
# data in the cache is as the domain owner intended, higher values,
# especially more than an hour or so, can lead to trouble as the data in
# the cache does not match up with the actual data anymore
cache-min-ttl: 300
cache-max-ttl: 86400
# Have unbound attempt to serve old responses from cache with a TTL of 0 in
# the response without waiting for the actual resolution to finish. The
# actual resolution answer ends up in the cache later on.
serve-expired: yes
# Harden against algorithm downgrade when multiple algorithms are
# advertised in the DS record.
harden-algo-downgrade: yes
# Ignore very small EDNS buffer sizes from queries.
harden-short-bufsize: yes
# Refuse id.server and hostname.bind queries
hide-identity: yes
# Report this identity rather than the hostname of the server.
identity: "Server"
# Refuse version.server and version.bind queries
hide-version: yes
# Prevent the unbound server from forking into the background as a daemon
do-daemonize: no
# Number of bytes size of the aggressive negative cache.
neg-cache-size: 4m
# Send minimum amount of information to upstream servers to enhance privacy
qname-minimisation: yes
# Deny queries of type ANY with an empty response.
# Works only on version 1.8 and above
deny-any: yes
# Do no insert authority/additional sections into response messages when
# those sections are not required. This reduces response size
# significantly, and may avoid TCP fallback for some responses. This may
# cause a slight speedup
minimal-responses: yes
# Perform prefetching of close to expired message cache entries
# This only applies to domains that have been frequently queried
# This flag updates the cached domains
prefetch: yes
# Fetch the DNSKEYs earlier in the validation process, when a DS record is
# encountered. This lowers the latency of requests at the expense of little
# more CPU usage.
prefetch-key: yes
# One thread should be sufficient, can be increased on beefy machines. In reality for
# most users running on small networks or on a single machine, it should be unnecessary
# to seek performance enhancement by increasing num-threads above 1.
num-threads: 1
# more cache memory. rrset-cache-size should twice what msg-cache-size is.
msg-cache-size: 50m
rrset-cache-size: 100m
# Faster UDP with multithreading (only on Linux).
so-reuseport: yes
# Ensure kernel buffer is large enough to not lose messages in traffix spikes
so-rcvbuf: 4m
so-sndbuf: 4m
# Set the total number of unwanted replies to keep track of in every thread.
# When it reaches the threshold, a defensive action of clearing the rrset
# and message caches is taken, hopefully flushing away any poison.
# Unbound suggests a value of 10 million.
unwanted-reply-threshold: 100000
# Minimize logs
# Do not print one line per query to the log
log-queries: no
# Do not print one line per reply to the log
log-replies: no
# Do not print log lines that say why queries return SERVFAIL to clients
log-servfail: no
# Do not print log lines to inform about local zone actions
log-local-actions: no
# Do not print log lines that say why queries return SERVFAIL to clients
logfile: /dev/null
# Ensure privacy of local IP ranges
private-address: 192.168.0.0/16
private-address: 169.254.0.0/16
private-address: 172.16.0.0/12
private-address: 10.0.0.0/8
private-address: fd00::/8
private-address: fe80::/10
server:
tls-cert-bundle: /etc/ssl/certs/ca-certificates.crt
forward-zone:
name: "."
forward-tls-upstream: yes
# Stubby
#forward-addr: 127.0.0.1@8053
#forward-addr: ::1@8053
# DNScrypt proxy
#forward-addr: 127.0.0.1@5353
#forward-addr: ::1@5353
# Quad9(Standard)
#forward-addr: 9.9.9.9@853#dns.quad9.net
#forward-addr: 149.112.112.112@853#dns.quad9.net
#forward-addr: 2620:fe::10@853#dns11.quad9.net
#forward-addr: 2620:fe::fe:10@853#dns11.quad9.net
# Quad9(ECS support)
#forward-addr: 9.9.9.11@853#dns11.quad9.net
#forward-addr: 149.112.112.11@853#dns11.quad9.net
#forward-addr: 2620:fe::11@853#dns11.quad9.net
#forward-addr: 2620:fe::fe:11@853#dns11.quad9.net
# OpenDNS
#forward-addr: 208.67.222.222@853#doh.opendns.com
#forward-addr: 208.67.220.220@853#doh.opendns.com
#forward-addr: 2620:119:35::35@853#doh.opendns.com
#forward-addr: 2620:119:53::53@853#doh.opendns.com
# Cloudflare
forward-addr: 1.1.1.1@853#cloudflare-dns.com
forward-addr: 1.0.0.1@853#cloudflare-dns.com
forward-addr: 2606:4700:4700::1111@853#cloudflare-dns.com
forward-addr: 2606:4700:4700::1001@853#cloudflare-dns.com
# Google
#forward-addr: 8.8.8.8@853#dns.google
#forward-addr: 8.8.4.4@853#dns.google
#forward-addr: 2001:4860:4860::8888@853#dns.google
#forward-addr: 2001:4860:4860::8844@853#dns.google
# AdGuard
#forward-addr: 94.140.14.14@853#dns.adguard.com
#forward-addr: 94.140.15.15@853#dns.adguard.com
#forward-addr: 2a10:50c0::ad1:ff@853#dns.adguard.com
#forward-addr: 2a10:50c0::ad2:ff@853#dns.adguard.com
what exactly is not working?
No
this is not possible
Question: did you removed AdGuard Home now? Because Unbound seems to LISTEN to port 53, which should not be the case if using AGH.
Next, our Unbound configuration file has not been changed since 3 years (DietPi 7.9). I’m wondering on your /etc/unbound/unbound.conf.d/dietpi.conf as it is quite different from the one we ship with our install script.
i installed 9.8.0 Adguard + Unbound (DOT)+ Clodflare . i was using that since 1 week
Today i updated 9.9.0. i see now i dont have internet.
Adguard looping when i reach http://192.168.1.48:8083
everything is working perfect 9.8.0 version.
As already said, your unbound configuration file seems to be different from our standard. Actually it seems using same port as AGH, which of course is not working. Did you manually changed the file?
yes i change it but everyhing already was using like that since 1 week.
thats unbound orginal configuration. i think i fixed it.
" interface: 127.0.0.1
port: 53 "
And when i backup dietpi . how can i restore it ?
When i try to restore backup . its give me error . it should restore on startup ?
i tried multiple time restore.
Simply run dietpi-backup and select restore. If there are errors, you would need to share them.
Probably you missed to restart Unbound after your changes done. As this is required for changes to take effect.
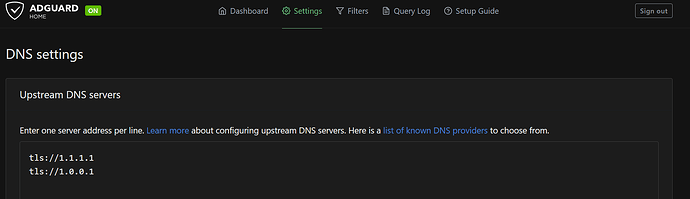
i fixed everything now. Thank you very much . dietpi works perfect. i use cloudflare
1.1.1.1
1.0.0.1
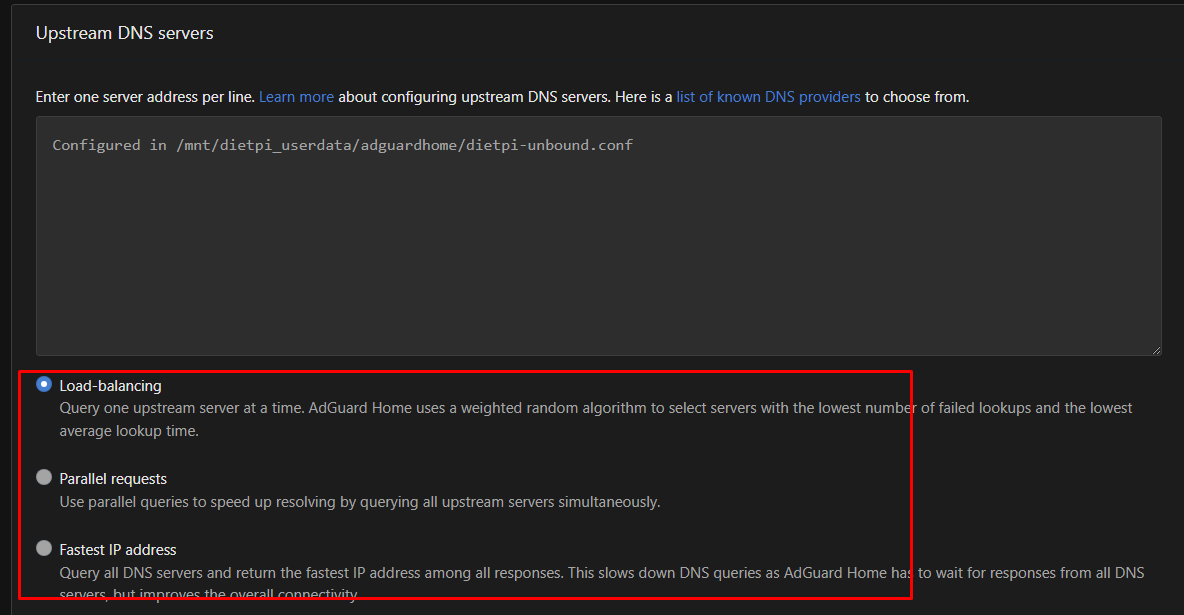
which one i need pick ? load-balancing or paralel request
This is completely irrelevant with the current configuration, as there is exactly one single upstream DNS server for AdGuard Home. And that is Unbound. How Unbound handles the settings and queries the DNS servers cannot be set in AdGuard Home.
One last note from me.
With your current Unbound configuration to use Cloudflare DoT, you have defeated the main purpose of Unbound, which is to use the DNS root servers. You don’t need Unbound for the pure use of DoT. This can also be set directly in AdGuard Home.
I understand that you said yes, there is no need for unbound for this, but when I did adguard (dot) + Cloudflare, I saw that Average upstream response time to high. I noticed that I received much faster responses when I had a configuration like adguard + unbound (dot) + cloudflare