just to avoid a misunderstanding. @MichaIng was pointing to the DietPi device hosting AGH. We usually advice to have DietPi network setting pointing to a global upstream DNS, and not to use the DNS service hosted on DietPi themself. ![]()
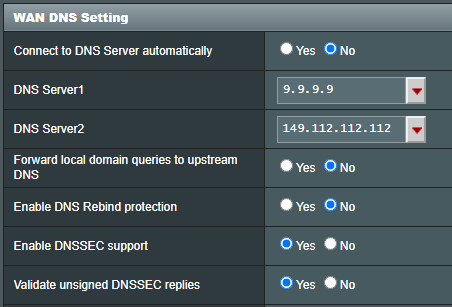
Ok, so when conducting a What’s My DNS IP, should it be showing my ISP’s DNS IP Address even when using AGH and Unbound? Forgot to mention that I am using Quad 9’s ‘9.9.9.9’ DNS IP Address as the WAN DNS IP on my router, but use the AGH IP for all LAN devices. I just don’t understand why I am still seeing my ISP’s DNS IP instead of something else…
Right - I meant that it is resolved via Unbound and the general traffic is pumped through WAN - I do understand this; thanks for the clarification.
Hmm, that is something that I have not been told. In the Network Settings of DietPi-Config, I use a static DNS IP of 127.0.0.1. I have had it like this for over a year without issues. - and I the AGH processing time hovers usually around 2.5-3ms. Isn’t it mainly for time syncing and updates?
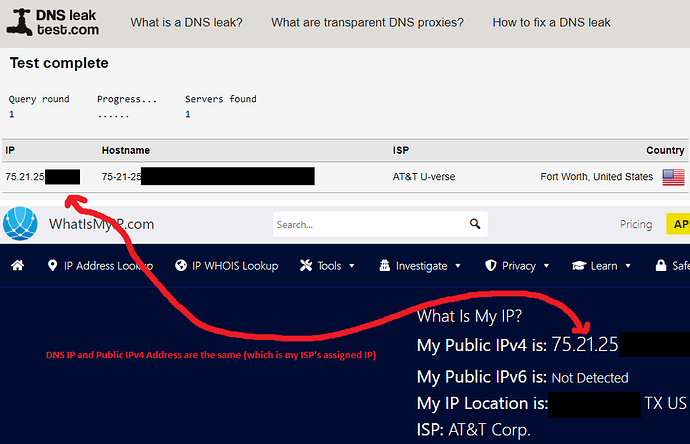
If I do a test using https://www.dnsleaktest.com/ it shows my own external IP address (https://www.whatismyip.com/) that has been assigned to my router and not the DNS server address my ISP is using. Switching Unbound to DoT, is correctly showing the DNS server I have defined as DoT server.
That’s all fine as long as it is working. But what happen if due to whatever reason, AGH and/or Unbound are failing? Usually your DietPi device will not be a able to update/install any application and you need to change network settings anyhow.
It’s basically our best practice, as we have seen people already knocking their head against the wall. Because they forgot about this setting and where wondering why DietPi software installs failed on the DNS check ![]()
Yes this your own external IP address and not a DNS server. Basically the same address you would use to connect to your home network from external.
Right, however since I am using Quad 9’s DNS Servers as my router’s WAN DNS, shouldn’t the DNS IP Address be showing as something other than my ISP’s IP address? See pics below…
When using Quad 9’s DNS IP on my travel router, a DNS Test usually shows one of Quad 9’s DNS IPs or domain name.
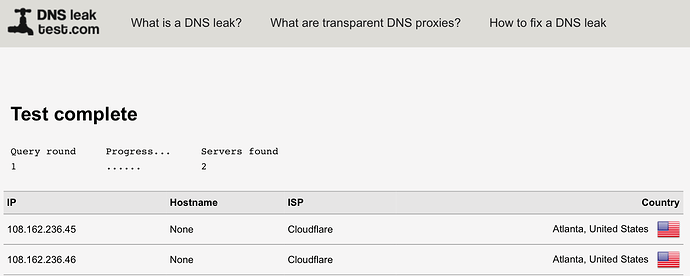
For example, I set my phone to use Cloudflares 1.1.1.1 (and turned off Wi-Fi so I am using Verizon’s LTE only) and I get this…
Settings in you router doesn’t matter as they are ignored by unbound. Better, unbound don’t care much on setting on your router. Unbound use whatever is defined on it’s configuration files. And Unbound is the one doing the DNS request towards the root DNS server. There is nobody in between. Therefore you are shown as DNS server ![]()
Ok, so let me make sure that I completely understand: If I am using my AdGuard Home and Unbound Server within my Router’s LAN DNS Settings, my external DNS IP will show as my ISP’s regardless if I have the Router’s WAN DNS Setting set to Quad 9?
It’s all about which DNS server is promoted to the client you do the test on:
- If you use a VPN or Tailscale (?), then it can force a DNS server, like AGH, which overrides the one possibly promoted by the DHCP server or assigned statically.
- Else, if you use a DHCP server, it will promote a DNS server, which can be usually configured in the DHCP server settings. Routers by default promote either an ISP DNS server to DHCP clients by default, or themself. If it’s themself, then the upstream DNS server of the router is used (which usually needs to be seen dedicated to the one promoted via DHCP, similar like the AGH is dedicated to DietPi’s own upstream DNS, while both can be the same when configured accordingly).
- Else if a static IP is assigned, then a static DNS along with it, and used accordingly.
On Linux systems, the currently used DNS server can be always seen in /etc/resolv.conf.
nearly correct. The important part for the behaviour is Unbound. Doesn’t matter of you use AGH, PiHole or no AdBlocker. As long as Unbound will be the one who is doing DNS resolution at the end, you will see your own external IP address on these DNS leak checks. Honestly I’m not 100% sure how these checks are done, but I assume they try to catch who is the last DNS resolver before the root DNS server. In case of Unbound, it is Unbound himself. There is no other upstream DNS server involved. Other than on your mobile phone where you use Cloudflare. There, of course you see Cloudflare as they do DNS resolution towards the root server.
If I am not mistaken, they make you resolve some domain name they control, e.g fgthfyghfghyyunytujhtyjayujyyjycd.example.com, and they check which one is the resolver querying for it. In case of unbound running on dietpi at home, it is going to be the public IP address of the connection, either the wan of the router or the CGNAT of the ISP.
Excellent information. Greatly appreciated!
Ok, so in conclusion:
- I decided to scrap the whole VPS with AGH and Unbound.
- My questions regarding DNS showing as the ISPs IP has been resolved.
- All is well in the world. Sort of.
Thanks again for the assistance.
P.S. - I decided to set up an OpenVPN Server on my ASUS Router (since Wireguard isn’t an option). It was extremely simple using the ASUS-WRT Merlin software. Almost too easy. I just turned it on, adjusted a few minor settings and downloaded the profile. I then uploaded it to the OpenVPN app on my iPhone, and BOOM it just worked. I had the opportunity to download the cert file as well but the app didn’t ask for it. Weird - but the profile is user/password protected so I suppose that’s enough security?
Yes, compared to WireGuard, OpenVPN uses user/password authentication for clients, the key for server authentication is usually part of the profile/ovpn config used/imported on clients. So choose a strong password.