System Security¶
Overview¶
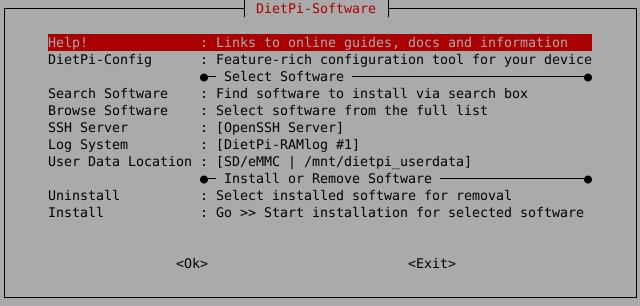
How do I run DietPi-Software and install optimised software items?
To install any of the DietPi optimised software items listed below run from the command line:
dietpi-software
Choose Browse Software and select one or more items. Finally select Install.
DietPi will do all the necessary steps to install and start these software items.
To see all the DietPi configurations options, review the DietPi Tools section.
Return to the Optimised Software list
Let’s Encrypt¶
Let’s Encrypt is a free SSL certificate provider. Certbot is the official client to apply Let’s Encrypt SSL certificates to your webserver. This will allow you to have https:// (encrypted and authenticated) access to your websites.
Requirements¶
To use Certbot you need:
- A working Apache, Nginx or Lighttpd webserver
- A URL/domain (e.g.:
mysite.org). No-IP can be used for a URL/domain that points to your device. - Ports 80 and 443 (TCP) need to be forwarded to your device. This is typically set within your router.
Keep port 80 open for Certbot renewal
Even when you use only HTTPS on port 443, Let’s Encrypt requires port 80 to stay opened for certificate renewals (in your router’s forwarding functionality).
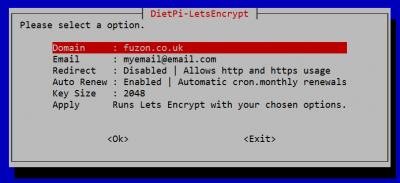
Create and apply your cert¶
Once Certbot has been installed from dietpi-software, run dietpi-letsencrypt to configure, create and apply your SSL certificate:
dietpi-letsencrypt
Simply enter the details and settings you require, then select Apply.
Let’s Encrypt is that simple!
Website: https://letsencrypt.org
Fail2Ban¶
Fail2Ban protects your system from brute-force attacks by banning the source IP address.
We have enabled detection for SSH servers (OpenSSH and Dropbear), however, Fail2Ban also supports additional software.

An IP address is by default ban triggered after 3 failed SSH login attempts. Fail2Ban will ban the source IP address for 10 minutes.
The status can be checked with these commands:
fail2ban-client status sshd
fail2ban-client status dropbear
Fail2Ban can handle several configuration options like general configuration and configurations for special programs on a config file base. The location of these config files is a directory structure within /etc/fail2ban/ and its subdirectories.
See the Fail2Ban documentation for further information including many filter configuration examples for programs.
Fail2Ban supports brute-force protection for other software, like Apache and ProFTPD. Pre-defined software filters can be found in the /etc/fail2ban/filter.d/ directory.
You can enable/disable these by adding additional [software] filter blocks to the /etc/fail2ban/jail.conf file, using the filters’ file names without file extension. Properties not defined in a specific filter block, are taken from the [DEFAULT] block.
See also the Fail2Ban configuration examples for vsftpd and ProFTPD.